NIS2 #14: Software Audit
See how to effectively manage licenses and compliance in eAuditor
NIS2 in a nutshell
With cyber threats on the rise, preparing a crisis management plan has become one of the key steps to ensure security in accordance with the NIS2 directive. Neglecting this area can lead to delayed incident response and serious operational losses.
Crisis management plan as key to NIS2-compliant security
The preparation of a crisis management plan has become an indispensable component of an NIS2-compliant security strategy. From the data ENISA shows that only 45% of companies has up-to-date incident response procedures, which means that most organizations risk a delayed response in the event of a cyber attack. Indications are that having comprehensive crisis management plans in place can reduce incident response times by more than 50%, allowing for faster recovery and reduced operational losses.
The contingency plan should include action scenarios for different types of incidents, clearly assigned roles and responsibilities, and rules for communicating with key stakeholders, including regulators and customers. This kind of preparation increases the organization’s resilience to threats and demonstrates the company’s commitment to NIS2 requirements, which in turn improves its reputation in the market.
How to meet NIS2 requirements with eAuditor?
Software audit
USE CASE
Due to the implementation of the NIS2 regulations in the unit, it became necessary to audit the installed software.
Responding to the requirements of Articles 21 and 23 of the directive, the unit has taken steps to comply with the requirements for security audits, software monitoring and license management.
As a result, it was necessary to centralize the monitoring and auditing system for the software already installed.
To meet the requirements of the directive, the Auditor system was prepared and implemented to audit installed software and account for licenses.
To this end:
- A system agent was installed on the computers.
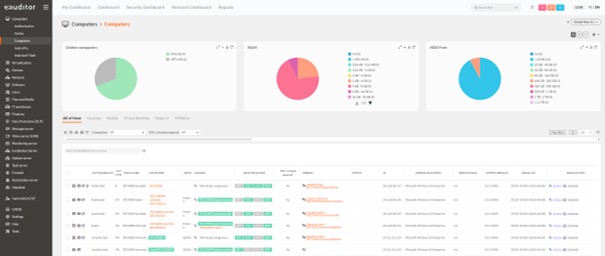
- Then in the system eAuditrack machine scanning was carried out. It allowed it’s on the gatheringe information about installed software on computers in the organization.
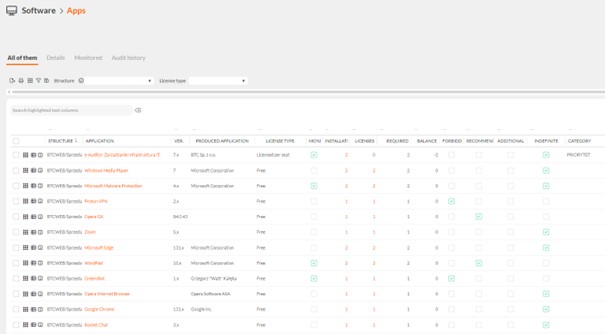
- Then you entered the licenses for your software into the system and ran the optionę software conversion, which This allowed to determinee license balance.Thanks to this, the system provides the ability to perform a quick and complete audit of installed software and owned licenses. In the above way, the unit has raised its security standards in line with the rules of the NIS2 directive.
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: Is the crisis management plan mandatory?
Yes, NIS2 requires organizations to have up-to-date incident management plans, including clearly defined response procedures, assigned roles and communication policies.
Question 2: How does eAuditor help meet NIS2 requirements?
System eAuditor enables real-time monitoring of activity, rapid detection of incidents and generation of detailed reports to support the implementation of security requirements under the directive.
Question 3: Does eAuditor support software and license auditing?
Yes, eAuditor enables a thorough audit of installed software and license compliance checks. This enables the organization to meet NIS2 requirements for software oversight and IT security.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!