NIS2 #13: Firewall management
Central firewall management in light of NIS2 directive requirements
NIS2 in a nutshell
The NIS2 directive not only changes the way organizations manage cyber security, but also places great emphasis on transparency with customers. Openness in reporting cyber security incidents is becoming crucial to build and maintain trust among customers. Is your organization prepared to meet the new requirements and use transparency as an asset in the market?
Transparency as the key to customer trust
The NIS2 directive is changing the way companies approach transparency with customers, especially in the context of reporting cyber security incidents. According to a PwC report, companies that communicate openly with customers about incidents and security activities see an increase in customer trust, which translates into greater loyalty and a positive image. The Deloittedreport found that 62% of customers say they prefer to work with companies that are transparent about security issues. Such openness not only allows companies to comply with NIS2 requirements, but also becomes a strategic element of differentiation in the market. Transparency in incident management is particularly important in sectors where customer trust is key, such as finance, health and digital
How to meet NIS2 requirements with eAuditor?
Firewall management
USE CASE As the unit implemented the provisions of the NIS2 directive, it became necessary to implement a tool to monitor and manage firewall settings on computers in the organization. Responding to the requirements of Article 23 of the directive, the unit prepared to centrally manage firewall settings on all computers in the unit. To meet the requirements of the directive, the eAuditor system was prepared and implemented to meet the requirements for monitoring threats and blocking suspicious activity. To this end:
- A system agent was installed on the computers.
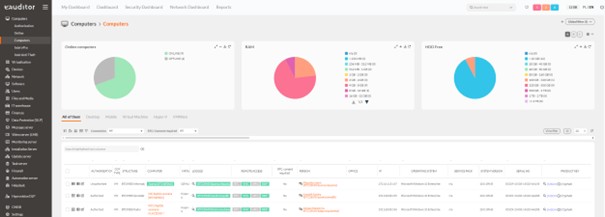
- Next, a scan of the machines was performed in the eAuditor system. This allowed the Firewall tab to display all rules active on the end computers.
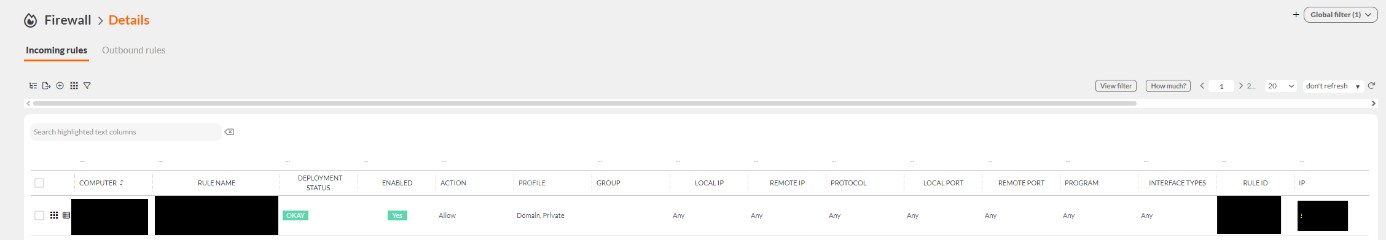
- Thus, the system provides central and secure management of firewall settings.In the above way, the unit has raised security standards by subscribing to the rules of the NIS2 directive. Learn more about firewall management https://www.eauditor.eu/zdalne-zarzadzanie-zapora-firewall
NIS2 – Meet answers to questions
Q&A Section Due to numerous questions about NIS2, we have prepared a comprehensive list for you to answer the most pressing issues related to the directive. Question 1: What are the benefits of transparency to customers in the context of NIS2? Transparency on cyber security issues allows organizations to increase customer trust, which translates into higher loyalty and a positive corporate image. Companies that openly communicate with customers about incidents not only meet NIS2 requirements, but also build reputation, which becomes their competitive advantage, especially in sensitive sectors such as finance or health. Question 2: What transparency changes does the NIS2 directive impose?
The NIS2 directive makes it mandatory to report security incidents to relevant authorities, but also emphasizes the need to communicate with customers about cyber threats. Organizations need to be more open, which translates into trust and minimizing reputational risk. Question 3: Does the use of eAuditor affect the company’s reputation?
Yes, implementing eAuditor helps companies maintain high security standards, which has a direct impact on customers’ perceived responsibility and professionalism. Transparency of security operations increases the level of trust and positively affects the image of the organization, which is especially important in times of increasing cyber threats.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!