NIS2 #12: Employee monitoring
Labor monitoring in light of the new requirements of the NIS2 directive
NIS2 in a nutshell
Employee awareness is the first step in protecting against cyber threats, and the NIS2 directive places special emphasis on employee education. Is your organization prepared for the new responsibilities for training and monitoring employee activity?
Learn how to improve cyber security through regular training and implementation of solutions such as eAuditor that meet NIS2 requirements and minimize the risk of incidents.
Employee education key to cyber security
The NIS2 directive emphasizes the role of educating employees at all levels of an organization in protecting against cyber threats. More than 60% of companies in Europe admit that their personnel are not sufficiently prepared to respond to such threats.
To reduce the risk of human error, NIS2 makes regular training mandatory:
- Recognizing threats, such as phishing.
- Procedures for handling Incidents.
- Data protection and compliance with security policies.
Companies that invest in staff education are better able to meet NIS2 requirements, minimizing the risk of attacks, data leaks, financial penalties and reputational damage. Regular training increases employee awareness and readiness, which is the foundation for effective cyber security management.
How to meet NIS2 requirements with eAuditor?
Monitoring of employees
USE CASEIn connection with the implementation of the NIS2 regulations in the unit, it became necessary to monitor the activity of the unit’s employees.
Responding to the requirements of Article 23 of the Directive, the unit has prepared itself to perform monitoring and detection of threats, through ongoing monitoring of user activities and identification of unauthorized actions.
To comply with the directive, the unit prepared and implemented the eAuditor system, which allowed it to monitor user activity and create a complete action log. This will allow the unit to meet both security requirements and raise the level of security in the system, as well as to report if security incidents arise.
- A system agent was installed on the computers.
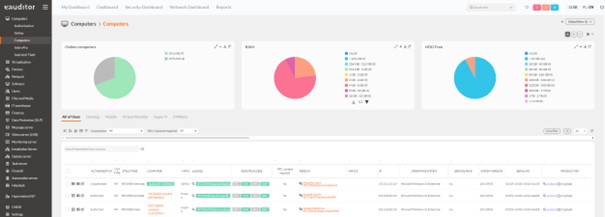
- Then in the eAud systemitrack configuration was preparedę providing complete activity monitoring and distributed it to the computers.
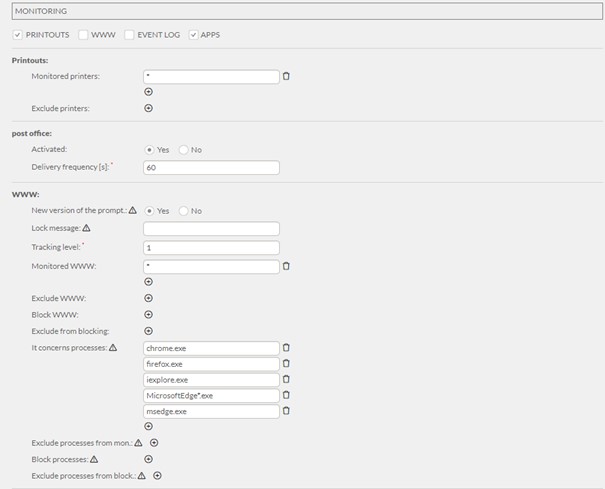
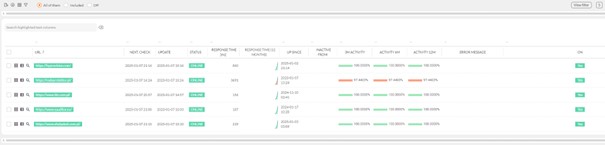
- After the initial scan, the agent allowed real-time activity to be monitored in multiple monitoring views of the monitoring server.
Thus, the system will ensure that the user logs in and records the action.
In the above way, the unit has raised its security standards by subscribing to the rules of the NIS2 directive.
NIS2 – Meet answers to questions
Q&A Section Due to numerous questions about NIS2, we have prepared a comprehensive list for you to answer the most pressing issues related to the directive. Question 1: What employee education requirements does the NIS2 directive impose?Directive NIS2 requires regular training for employees at all levels of the organization. This training must include, among other things, threat recognition (e.g. phishing), incident handling, and adherence to security policies.Question 2: How does eAuditor support organizations in monitoring employee activity?
eAuditor enables ongoing monitoring of user activities, identifying unauthorized actions and creating a complete activity log. This enables organizations to respond quickly to potential incidents and meet the requirements of Article 23 of the NIS2 Directive.
Question 3: Is it legal to monitor employee activity?
Yes, monitoring user activity using eAuditor is carried out in accordance with the law, provided that appropriate procedures for informing employees and adhering to privacy rules are followed.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!