NIS2 #10: BitLocker disk encryption
Find out if your organization is ready for change
NIS2 in a nutshell
The NIS2 directive requires organizations to thoroughly assess their IT security. A cyber security audit is the first step to identify security gaps, develop a plan to comply with the new regulations, and avoid financial penalties and operational problems . Sprawdź, czy Twoja organizacja jest gotowa na zmiany.
Cyber security audit as a key element of NIS2 implementation
Implementing NIS2 requires a comprehensive IT security assessment, and a cybersecurity audit is a key step to make it happen. It allows you to assess the state of your security, identify gaps and develop a plan tailored to NIS2 requirements. The audit includes an analysis of security policies and an assessment of monitoring systems. It helps prepare for an audit, identify infrastructure vulnerabilities and plan corrective actions. Organizations that conduct audits gain greater awareness of risks, implement NIS2 more effectively and build trust with customers and partners. Failure to prepare for NIS2 can result in penalties and operational problems, so auditing is key to achieving compliance with the new regulations.
How to meet NIS2 requirements with eAuditor?
BitLocker disk encryption
USE CASE
Due to the implementation of the NIS2 directive in the unit, it has become necessary to encrypt drives The NIS2 directive stipulates the need to take care of the unit’s data security, in particular to encrypt hard drives en masse throughout the organization. Such an operation can be time-consuming and problematic. The eAuditor system allowed the unit to carry out mass encryption using the system and its agents to perform the action silently, without involving end users. In addition, disk recovery keys were secured and encrypted. This allowed the company to meet the requirements of Article 21 of the directive requiring data protection and risk management, which indicate the need to encrypt special category data. To this end:
- A system agent was installed on the computers.
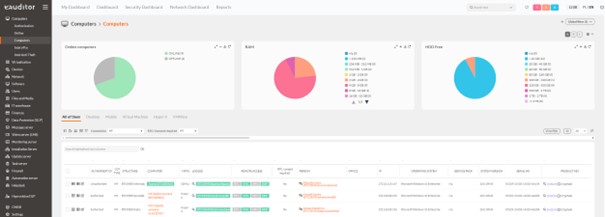
- Then, in the eAuditor system, after the hardware scan, the BitLocker disk encryption command was distributed using the device view option -> hard drives.
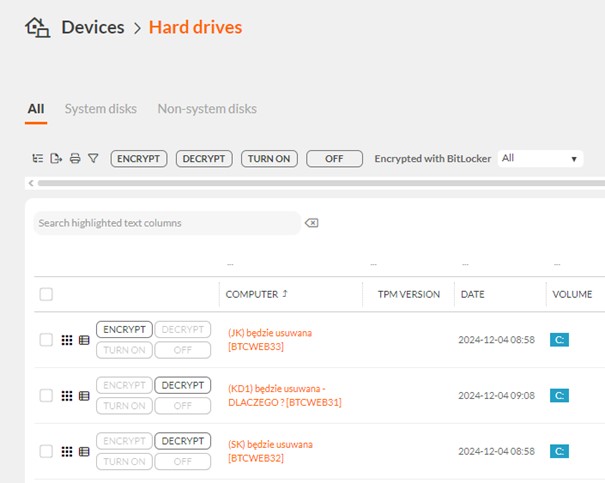
- Thanks to this, the system will automatically start encrypting the defined drives using the selected encryption method.This will protect the data by automating the process of encrypting the media, protecting the unit from data leakage.In the above way, the unit has raised the security standards by subscribing to the rules of the NIS2 directive.Learn more about controlling the used applications in the eAuditor system – https://www.eauditor.eu/blokowanie-aplikacji/
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: What are the benefits of BitLocker bulk disk encryption?
Encryption of hard drives protects special category data from leakage, meets the requirements of Article 21 of the NIS2 Directive and increases the security level of the organization. With eAuditor, this process can be carried out in bulk and automatically, minimizing disruption to users.
Question 2: Is USB and disk encryption an obligation under NIS2?
Yes, NIS2 requires the use of encryption as a means of protecting special category data and managing risk. This applies to both USB drives and hard drives, helping to prevent data loss in the event of loss or theft.
Question 3: How does a cybersecurity audit help prepare for NIS2 implementation?
The audit enables an assessment of current safeguards, identification of gaps and development of a plan to comply with NIS2 requirements. It also helps prepare the organization for future audits and increases awareness of risks.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!