NIS2 #8: Software monitoring
Find out how to identify installed software on devices
NIS2 in a nutshell
With the NIS2 directive coming into effect, entities in a variety of sectors need to adapt their IT systems to the stricter data protection and cybersecurity requirements. In this email, we outline how NIS2 supports data protection and what solutions can help ensure compliance with the new regulations.
Energy industry
Securing data and privacy has become a priority for companies due to growing cyber threats and new legal requirements. The NIS2 Directive, which supplements the RODO, imposes additional requirements for protecting information in companies. According to a Gartner report, more than 60% of entities admit that processing data is becoming a challenge due to its growing volume and new regulations. NIS2 requires security measures such as data access monitoring and advanced incident reporting procedures. Experts point out that a key element of NIS2 is risk management and protecting data from unauthorized access. Companies need to implement technologies to monitor and analyze data traffic in real time. Meeting the requirements of NIS2 also brings reputational benefits, enhancing an organization’s credibility. Compliance with these regulations helps avoid financial penalties and protect against image damage. Companies that have not yet implemented NIS2-compliant solutions should adapt their data protection procedures as soon as possible.
How to meet NIS2 requirements with eAuditor?
Software control
USE CASE
Due to the implementation of the NIS2 directive provisions in the entity, it has become necessary to control the software installed on devices. The NIS2 directive imposes an obligation to monitor and manage the software in use, both in terms of inventory and security. According to Art. 21 directive, it is also necessary to eliminate the risks arising from the use of unauthorized software. To meet these requirements, the unit decided to use the eAuditor system for software control.
- The eAuditor system agent was installed on the computers.
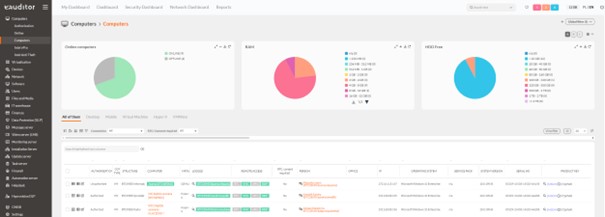
- A device scan command was sent out on the system to create a complete list of installed software.
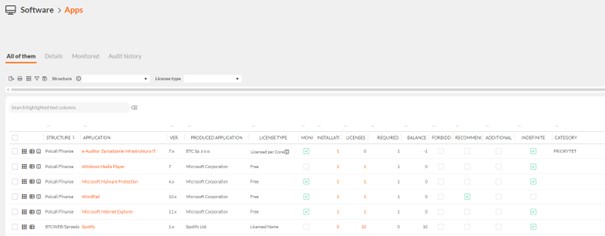
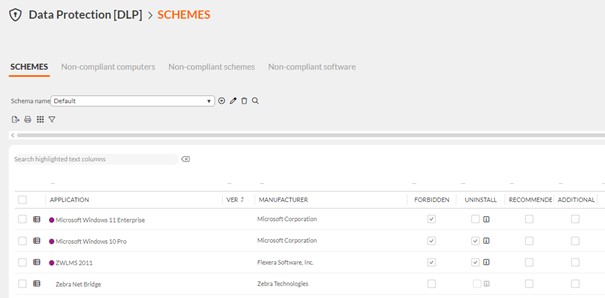
- A data protection function (DLP) was used to automatically identify and remove unsafe or unauthorized applications.Through these measures, the unit gained full control over the software in use, ensuring compliance with NIS2 requirements and effectively minimizing the risk of unauthorized applications.
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: What steps do I need to take to comply with data and privacy requirements?
Meeting NIS2’s data protection and privacy requirements requires organizations to audit data, implement encryption and access controls, use Data Loss Prevention (DLP) systems, manage user permissions, and regularly train employees and ensure incident preparedness. Regular monitoring and audits maintain compliance and strengthen the organization’s data protection.
Question 2: Does the NIS2 directive require security incident reporting? How can eAuditor help with this?
Yes, NIS2 requires that cyber security incidents be reported to the appropriate authorities within 24 hours of detection. The eAuditor helps monitor activity in systems and automatically detect potential incidents, allowing for rapid response and reporting as required by the directive.
Question 3: Is having a full software inventory required by NIS2?
Yes, according to NIS2, entities must have a complete software inventory to monitor compliance and eliminate the risk of unauthorized applications. eAuditor automatically scans devices and creates an updated software list, simplifying the inventory process.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!