NIS2 #7: USB monitoring
Learn how to monitor USB drives used by employees
NIS2 in a nutshell
The health sector is one of the key areas covered by the NIS2 directive, which means new challenges and responsibilities related to patient data security. Does your company fully understand what these changes mean and how to prepare for them? Read more to secure your infrastructure and meet NIS2 requirements.
Changes in the health sector
NIS2 makes it mandatory to protect medical infrastructure and patient data from cyber threats. There are financial penalties for failing to provide adequate safeguards, such as data encryption, which underscores the importance of information security in healthcare facilities. The new regulations require health facilities across the European Union to use modern data protection technologies, such as intrusion detection systems and multi-step authentication, to reduce the risk of cyberattacks. The regulations also aim to standardize security standards in the health sector, making medical infrastructures more resilient to new and increasingly sophisticated threats. This gives the health sector an extra layer of protection to prevent data leaks and safeguard patient privacy.
How to meet NIS2 requirements with Hyprovision DLP?
USB monitoring
USE CASE
In connection with the implementation of the NIS2 directive provisions in the unit, it has become necessary to monitor the USB drives used by employees. The provisions of the NIS2 Directive require the provision of adequate data protection measures to avoid uncontrolled data sharing. These requirements are in line with Article 21 of the directive, which requires eliminating the risk of unauthorized copying of data. To this end, the unit decided to implement the Hyprovision DLP system .
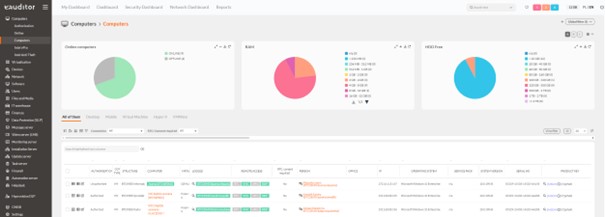
- The Hyprovision DLP system agent was installed on the computers.
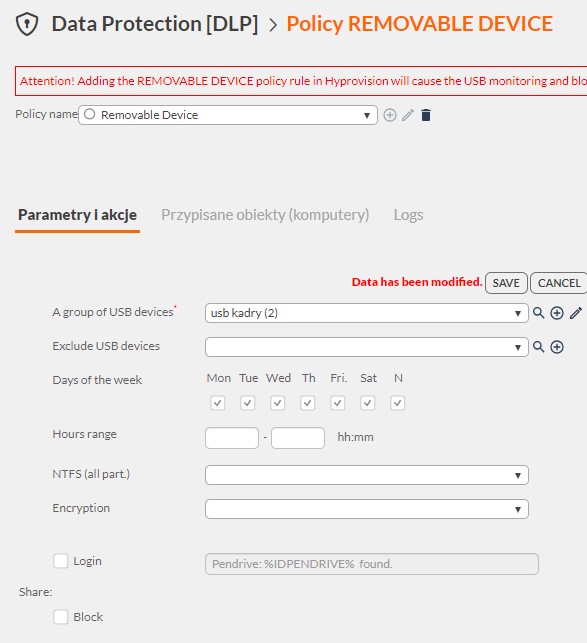
- Hyprovision has prepared a DLP Removable device policy, blocking all unencrypted USB drives.
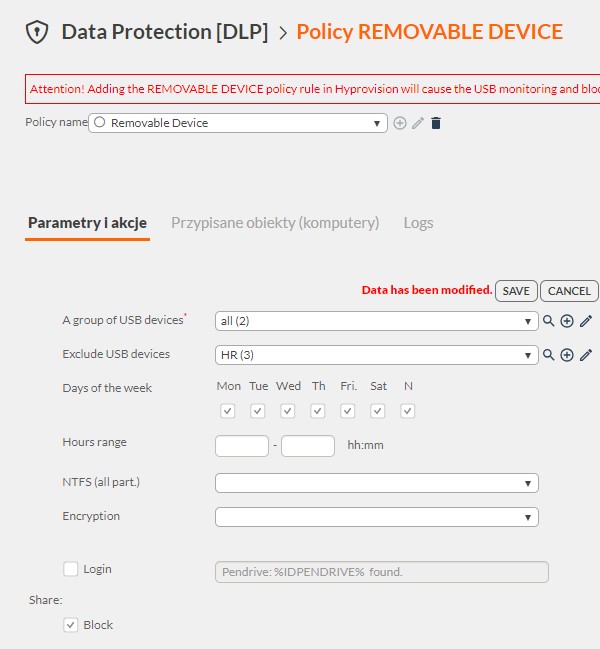
- Subsequently, a policy was created to block all unapproved USB media in the unit.With these measures, the unit effectively controls the use of USB media, eliminating the risk of unauthorized copying of data and ensuring compliance with NIS2 requirements.
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: What are the most important NIS2 requirements for the health sector?
NIS2 requires the health sector to manage cyber security risks, report incidents and implement strict safeguards such as data encryption and multi-factor authentication. In addition, it requires regular training for employees and cooperation with national regulators.
Question 2: What technologies can help secure patient data?
Technologies such as encryption and multi-factor authentication (MFA) help secure patient data. In addition, eAuditor enables real-time monitoring and auditing of data access to support security and compliance.
Question 3: Which health care facilities are affected by the NIS2 directive?
The NIS2 directive covers hospitals, clinics, medical laboratories, long-term care facilities and health IT system providers. It requires these facilities to implement risk management and data protection measures against cyber threats.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!