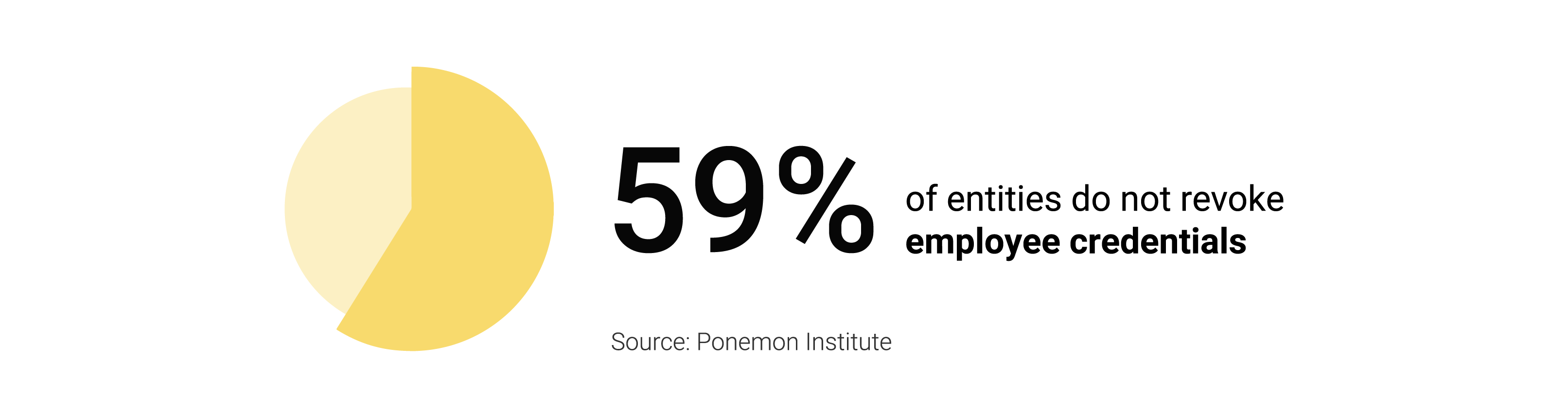
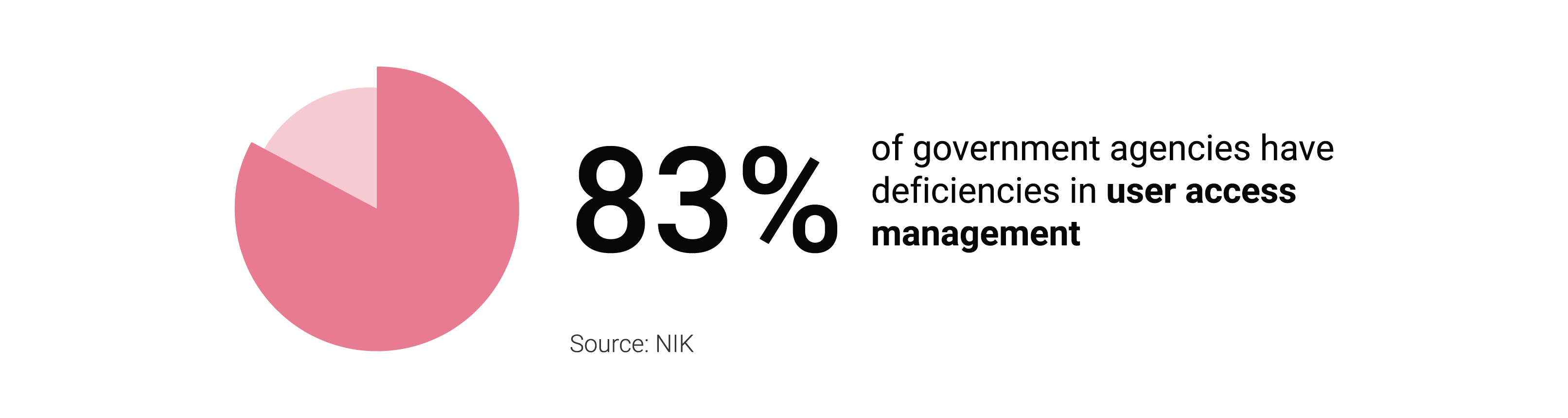
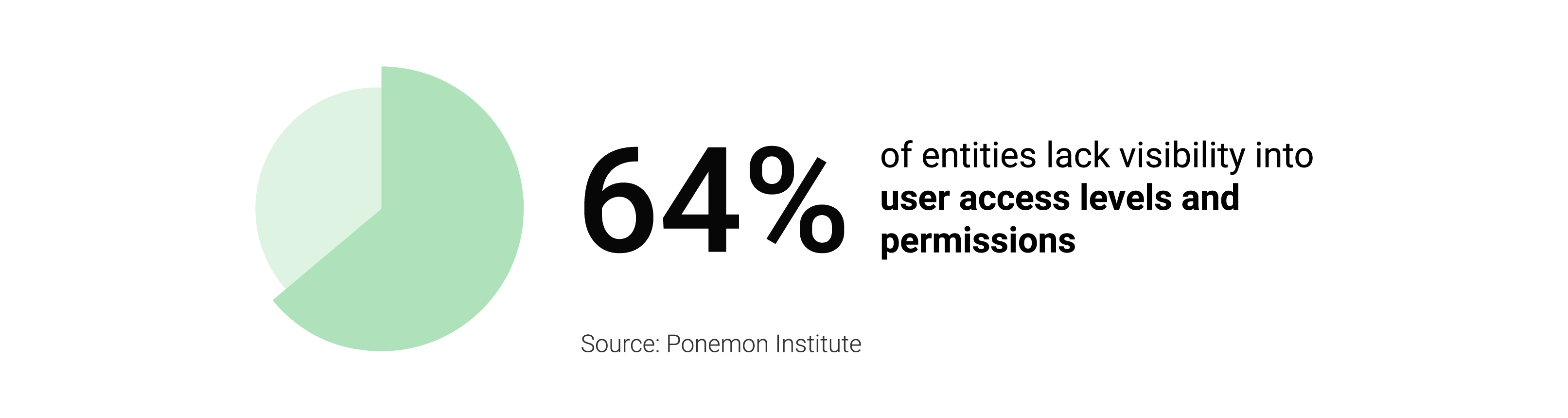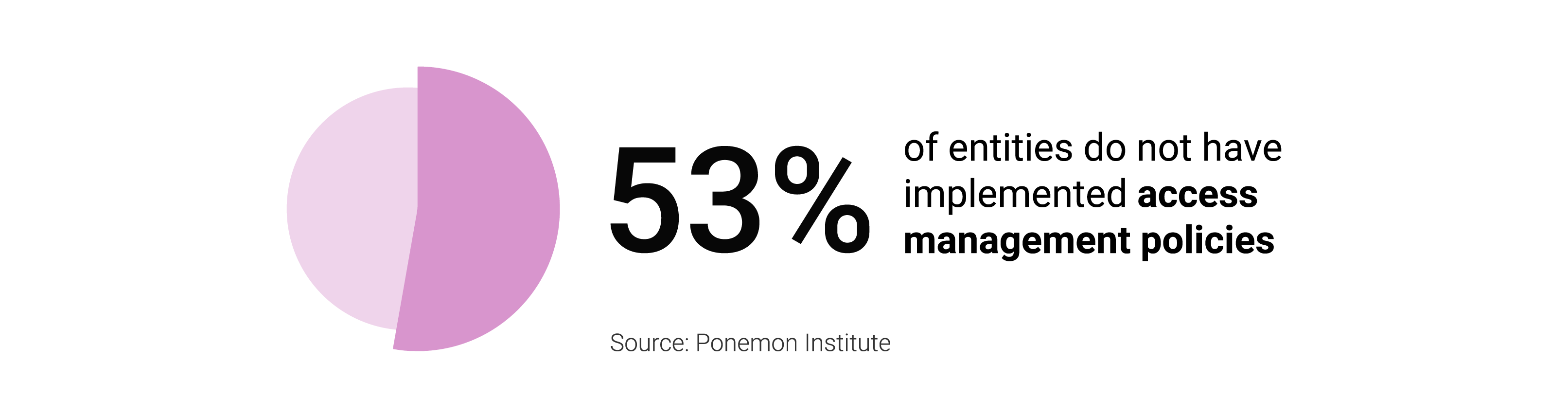Manage requests and permissions to IT systems
Manage requests and permissions to IT systems
Identity and Access Management (IAM) is the key to IT security. Grant, accept, monitor and audit assigned IT privileges
Identity and Access Management (IAM) is the key to IT security. Grant, accept, monitor and audit assigned IT privileges

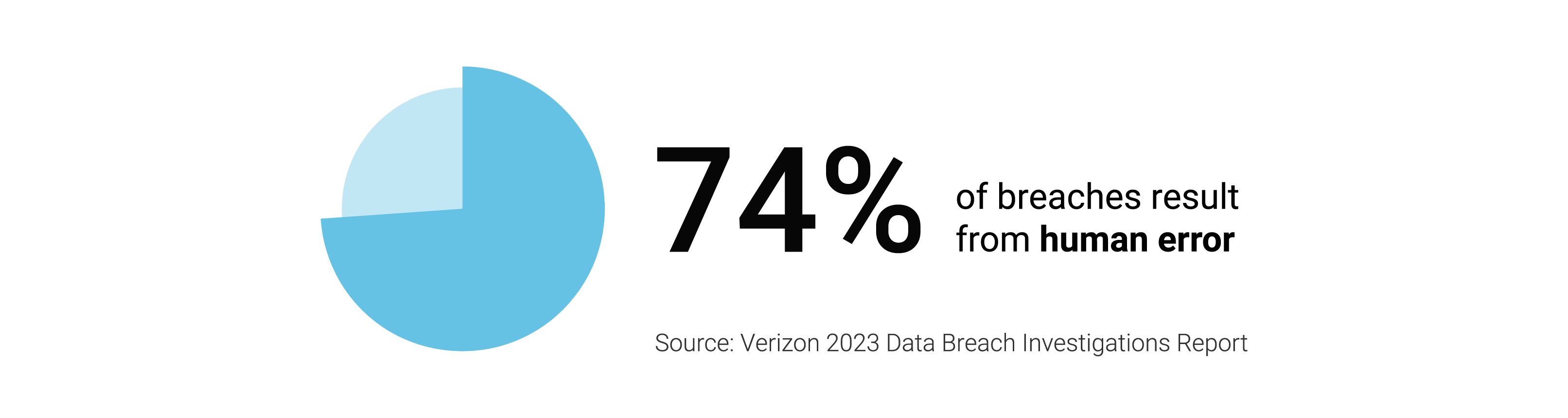
Did you know that…
Main functions
Benefits