User monitoring
- Computer Monitoring
- Activity Monitoring
- Document Monitoring
- Print Monitoring
Table of contents
User monitoring
This functionality involves monitoring the work of employees using various functionalities in the eAuditor system. They present data on user activity on computers located in the organization’s infrastructure using, among other things, artificial intelligence. They also monitor the permissions granted to employees for specific resources (local and network). They also allow you to obtain detailed information about the user logged on to the computer. In summary, the functionality is designed to analyze user behavior.
Monitoring of computers and working time
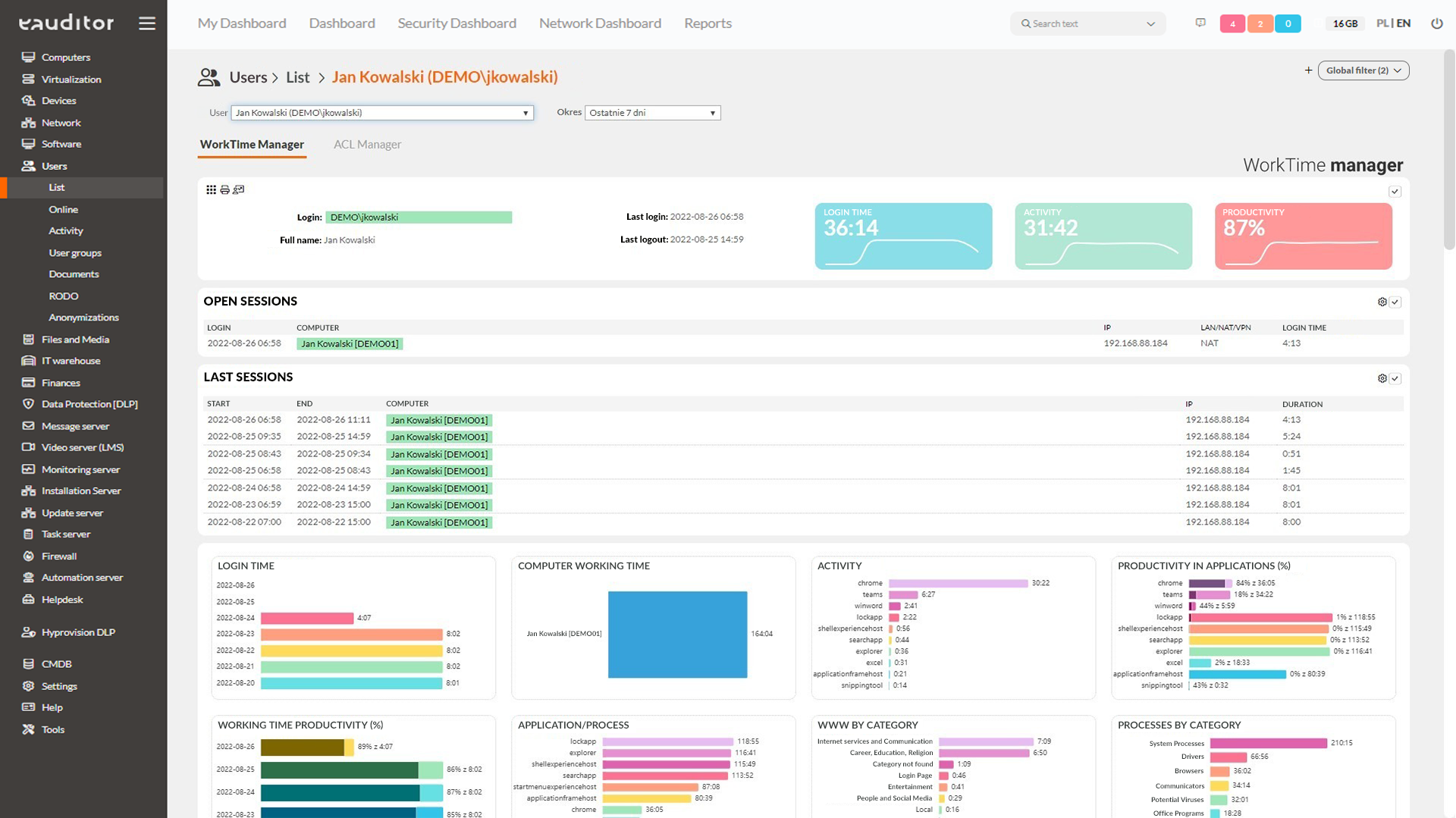
An employee performing his duties stationary in the office or while working remotely may receive one or more computers for use. Therefore, verifying the affiliation of equipment to specific individuals is very important from the point of view of minimizing the cost of purchasing equipment. WorkTime Manager allows the administrator to read the date of the last login on a given computer. With the appropriate definition of handover protocols, it is possible to view information about the affiliation of equipment to specific people. This functionality will allow not only to monitor working time, but aalso the extent of use of a given equipment by employees.
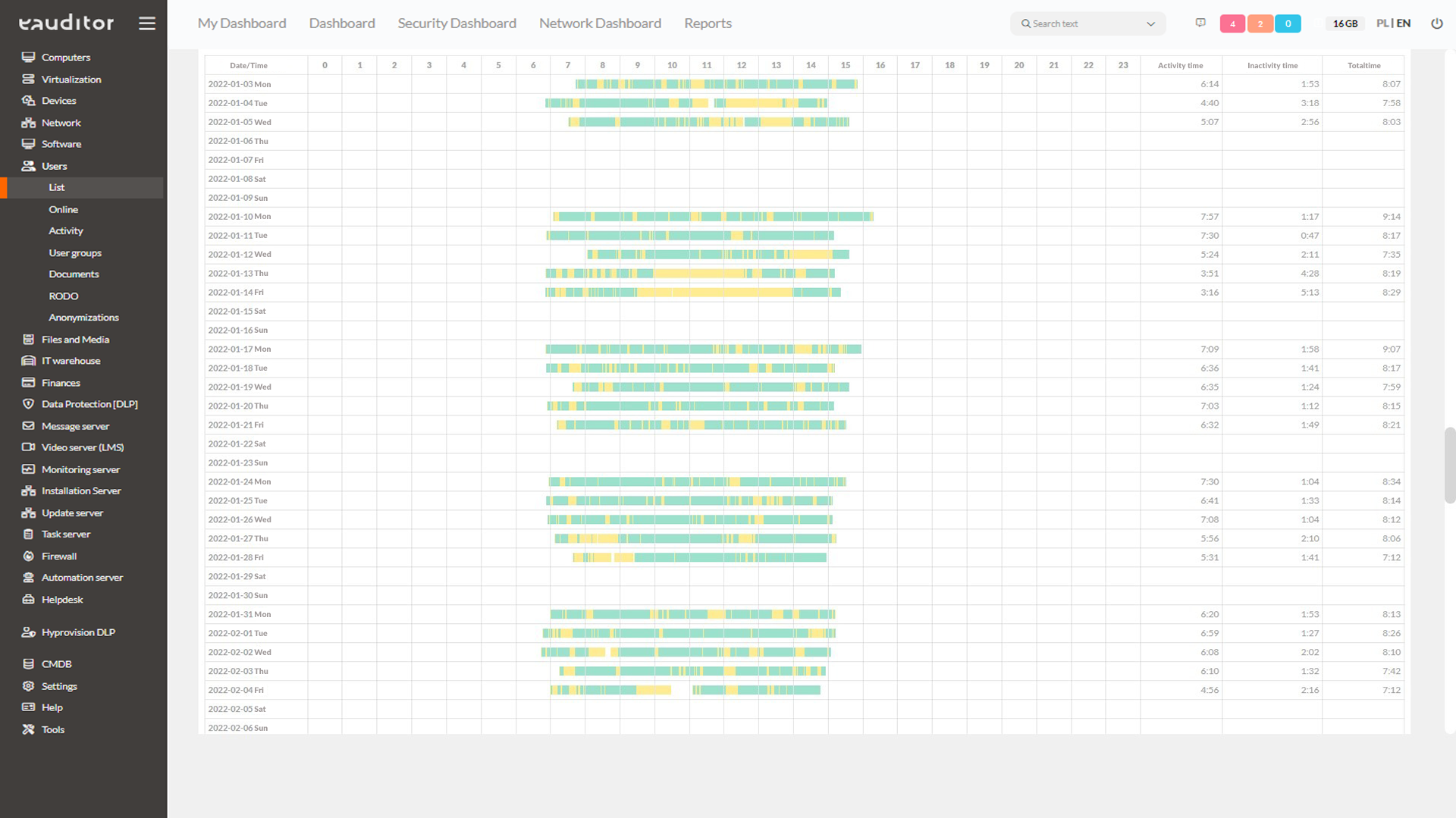
Activity monitoring
The administrator will effectively verify whether an employee is performing duties or browsing entertaining sites on company equipment. The eAuditor continuously analyzes users’ working time and computer logins, launched websites, connected devices (flash drives, external drives, multimedia devices), access to files, printed and sent documents. The eAuditor software therefore allows comprehensive control of employee activity on company hardware. This allows the administrator to analyze their productivity on an ongoing basis, based on aggregate data from a specific working day.
Monitoring website activity
Providing the highest level of security, the console provides real-time classification status information. The classification result includes, among others:
- indication of one of many predefined categories,
- presence on the CERT list,
- presence on the list of gambling sites,
- scanning to identify malware,
- analyzing the structure for security, having a valid SSL certificate.
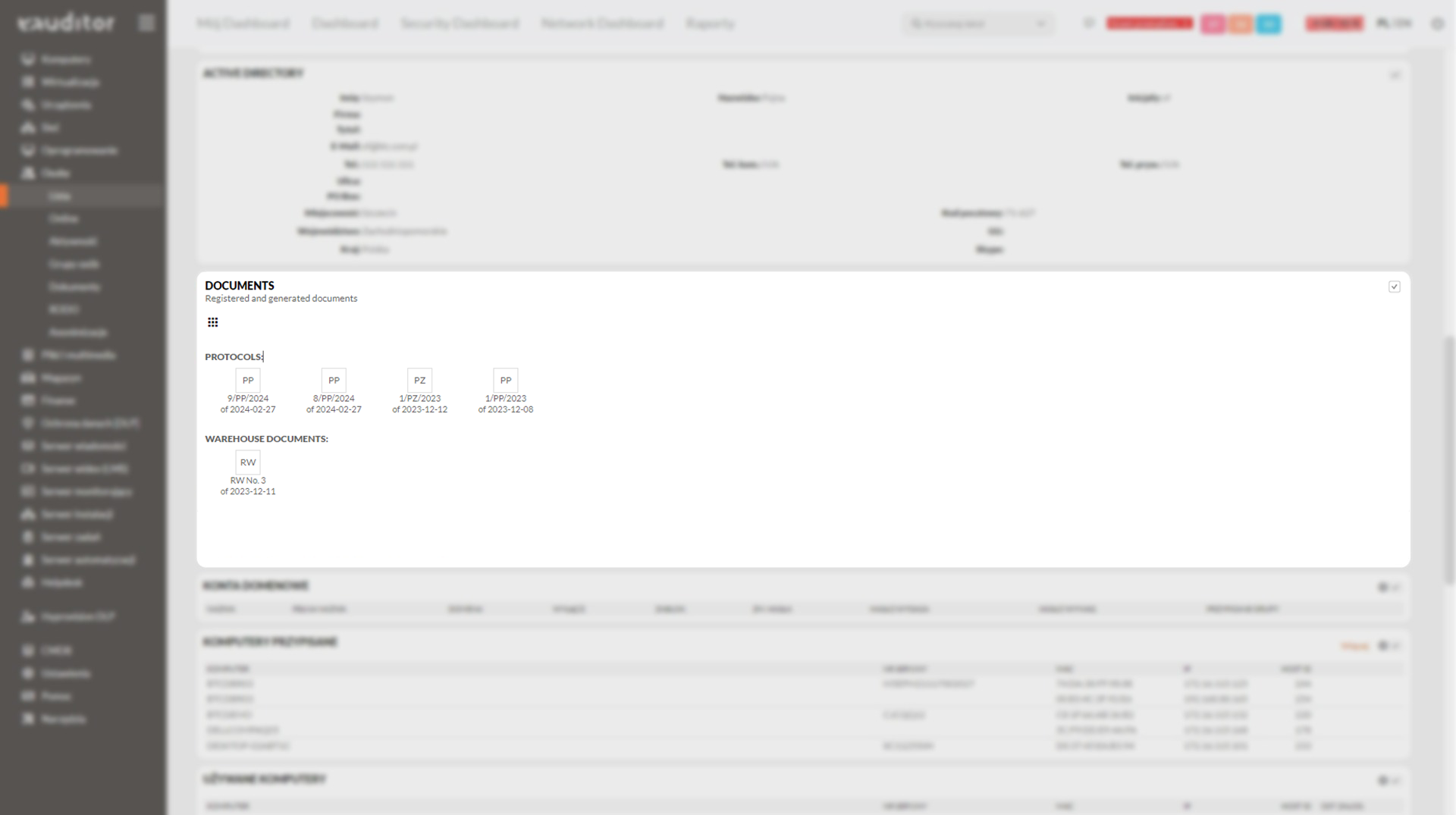
Document monitoring
In the eAuditor system, from the user’s detail card, it is possible to:
- modification,
- deletion,
- printing,
- adding necessary documents (handover, return, return-transfer protocols).
With a few clicks, the administrator will also generate handover protocol (PP), return protocol (PZ) and PZ+PP (return and handover protocol). Thus, he has quick access to the necessary information, registering and de-registering documents in the console.
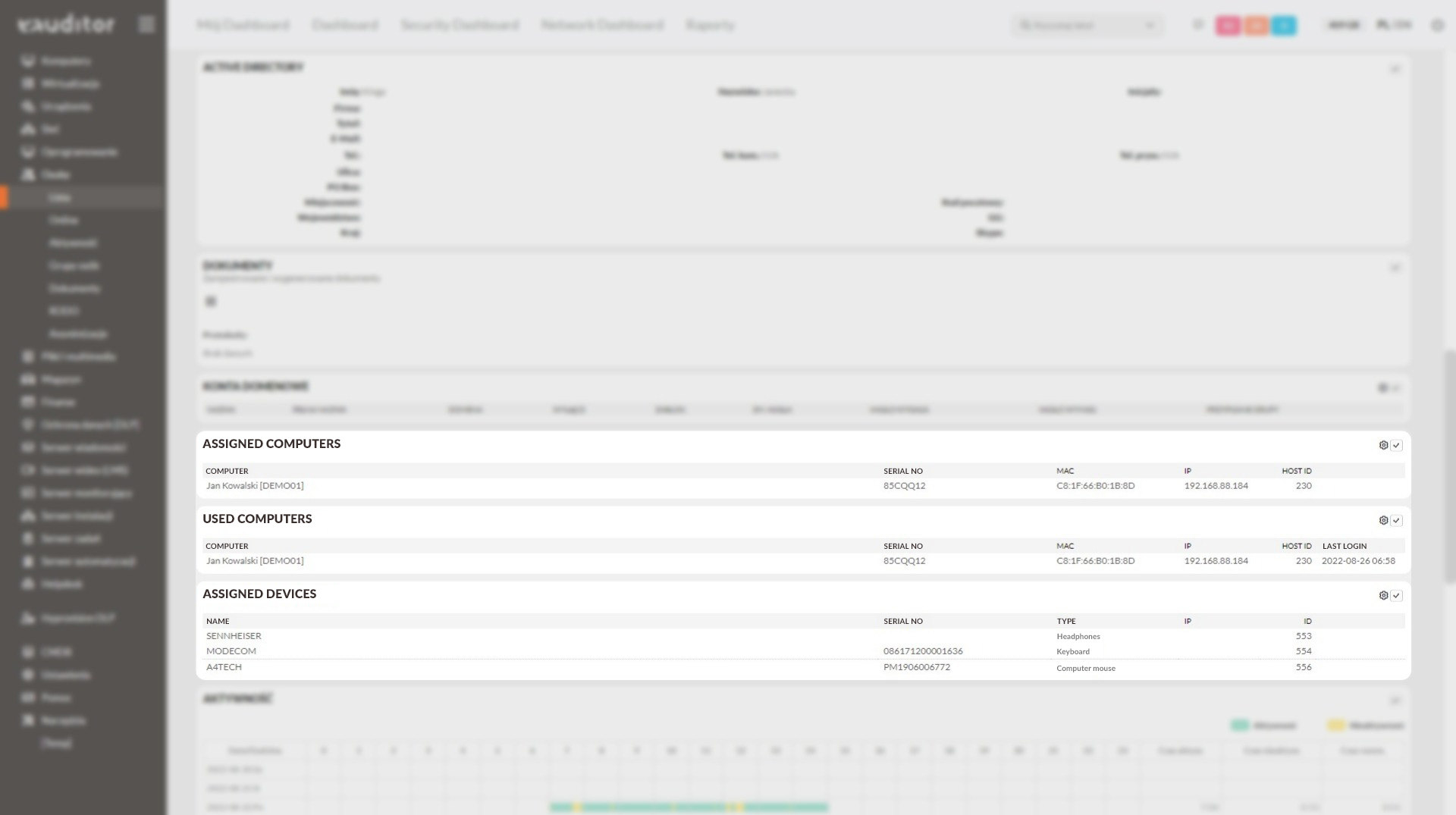
Device monitoring
In the eAuditor console, the administrator can view a list of devices assigned to employees. This can include information on printers, computers, monitors or flash drives This gives him full control over who is using the devices and who is responsible for them.
Monitoring of used software
It is possible to monitor licenses in the system in order to minimize software purchase costs. In WorkTime Manager, the administrator will verify whether the software has been used within the last 3, 6 or 12 months. In this way, he will easily check whether a particular department of the company is using the purchased software for the intended purpose and whether it is needed and actually exploited.
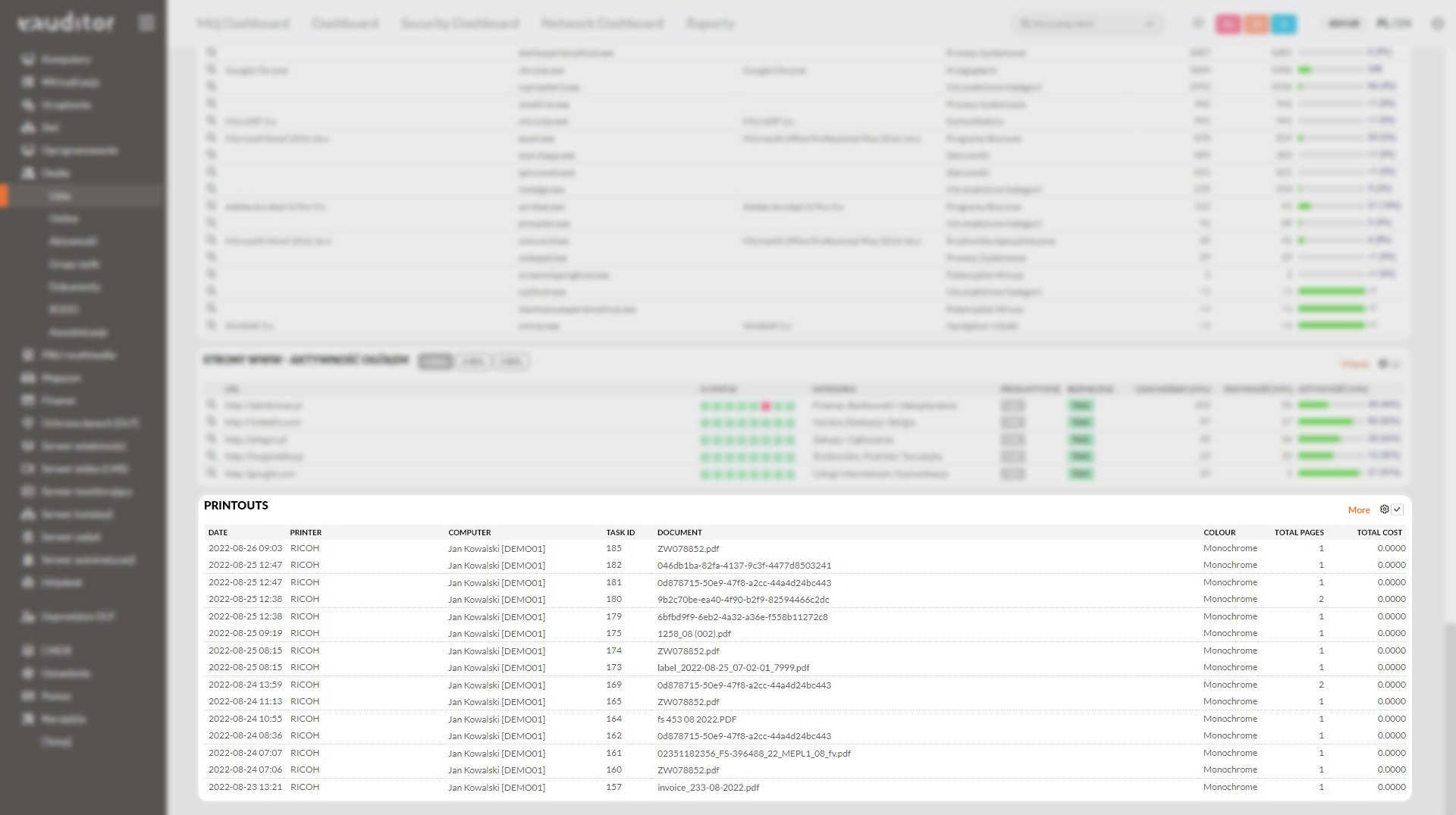
Monitoring of printouts
Managing the organization’s resources and using them efficiently is possible by monitoring the printouts made by employees. In WorkTime Manager it is possible to quickly check:
- document name,
- number of pages,
- types of printout (color/monochrome),
- date of printing,
- the cost of the printout.
In addition, the system monitors printouts made on the internal network and off the network, offering support for local and network printers. The software independently calculates the cost of printouts, according to parameters defined by administrators.
Monitoring domain accounts
In the eAuditor system, the administrator reads all domain accounts assigned to a given user. This is made possible by the eAuditor system’s full integration with Microsoft Active Directory. Thanks to this, in one place, the administrator will read the login information of a given user using a specific domain account.
Permission monitoring (ACL Manager)
The administrator can monitor user permissions to local and shared resources on an ongoing basis by using a special API. This allows him to analyze the accesses of employees (including those working remotely) from a fully web-based console. Within the ACL Manager functionality, it is also possible to access tabs presenting the following information about:
- users’ rights to folders,
- folders made available to users,
- users’ group memberships,
- user group rights to folders,
- owners of folders.
- It is also possible to select three groups of ACL d
- all – allow you to read all users, groups and folders authorized in the system,
- domain – allow reading domain users, domain groups and only shared fold,
- local – allow reading local users, local groups and local folders.
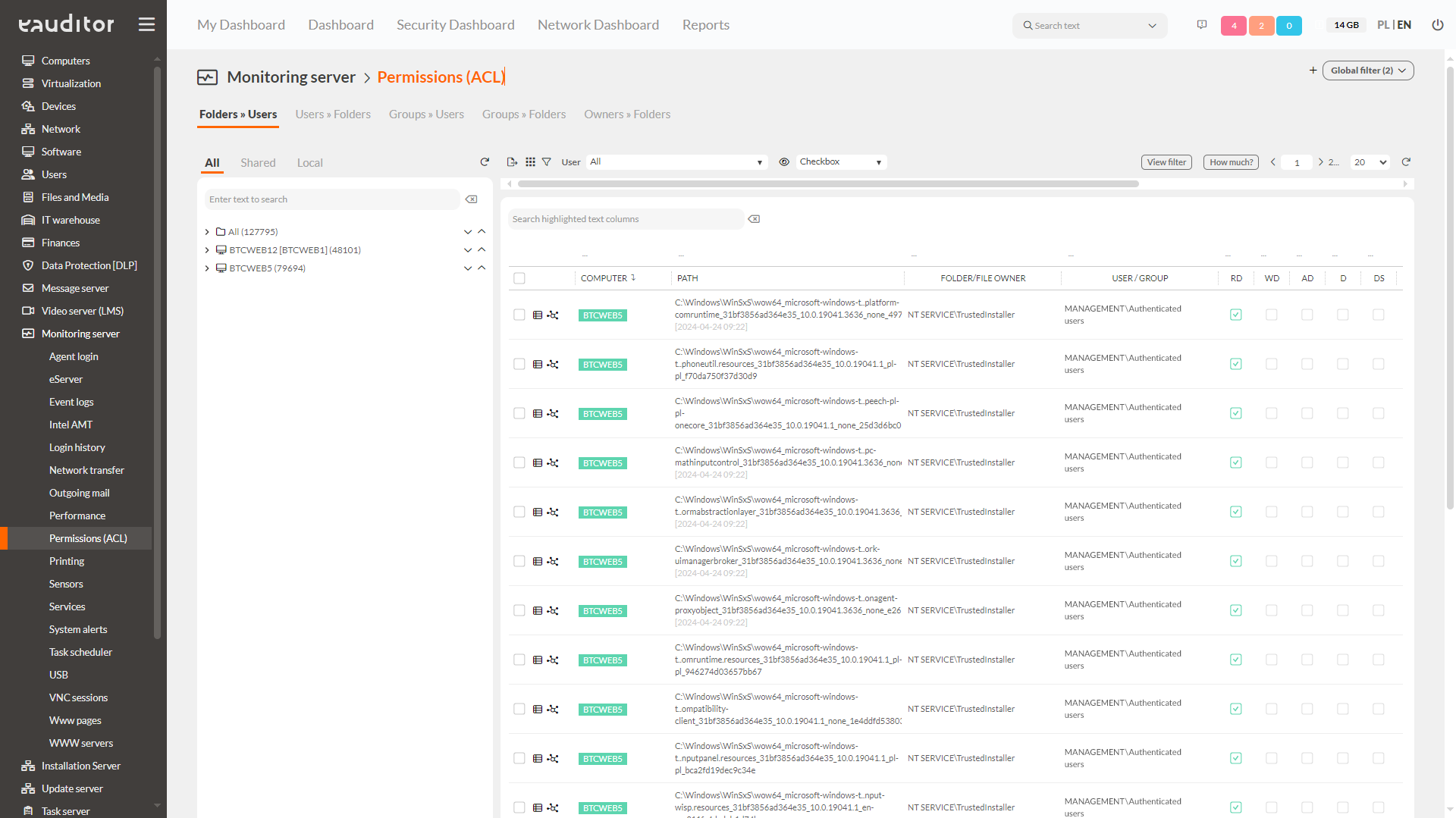
Thanks to the clear tree structure, it is possible to find the needed data even faster in the tables. This makes it easier to operate on sorted d
ACL Manager allows you to read 13 types of resource permissions:
- RD – Read Data specifies the right to read files.
- WD – Write Data specifies the right to open and write to a file or folder. This does not include the right to open and write file system attributes, extended file system attributes, and access and audit policies.
- AD – Append Data specifies the right to add data.
- D – Delete specifies the right to delete a folder.
- DS – Delete Subdirectories and Files specifies the right to delete a folder and any files contained in that folder.
- EF – Execute File specifies the right to run an application.
- RA – Read Attributes Specifies the right to open and copy file system attributes from a folder or file. For example, this value specifies the right to view the creation or modification date of a file. Does not include the right to read data, extended file system attributes or access and audit policies
- REA – Read Extended Attributes specifies the right to open and copy extended file system attributes from a folder or file. For example, this value specifies the right to view author and content information. It does not include the right to read data, file system attributes or access and audit rules.
- RP – Rea Premissions specifies the right to open and copy access and audit rules from a folder or file. It does not include the right to read data, file system attributes or extended file system attributes.
- WA – Write Attributes specifies the right to open and write file system attributes in a folder or file. It does not include the ability to write data, extended attributes and access and audit rules.
- WEA – Write Extended Attributes specifies the right to open and write file system attributes in a folder or file. It does not include the ability to write data, extended attributes and access and audit rules.
- CP – Change Permissions specifies the right to change security and audit rules related to folders.
- TO – Take Ownership specifies the right to change the owner of a folder. Note that owners of resources have full access to them.
Benefits
Want to learn more about this functionality? Read our article “Effective monitoring of computer and user activity”