USB blocking
- Managing USB Devices
- Blocking USB Devices using Whitelisting
- Blocking Unauthorized External Storage Devices
Table of contents
Why should you block USB drives?
By blocking the connection of USB devices from the administration console, employees will not be able to read unauthorized USB drives. Once a user plugs a device into a USB port, the system will prevent any action from being taken. As an additional protection, blocked flash drives will not be accessible at all in the system manager.
Benefits
USB media management
The administrator of the eAuditor system, from the administration console, has the ability to manage access to USB storage from business computers in the organization. For this to be possible, it is necessary to create so-called whitelists, that is, to define devices that are considered secure. This will automatically block all other USB storage devices connected to the computer.
Blocking USBs using whitelisting
From the console, the administrator can define a rule to block unauthorized flash drives. To do so, he needs to take several steps related to enabling USB monitoring, verifying connected devices and creating whitelist rules.
Blocking USB in eAuditor
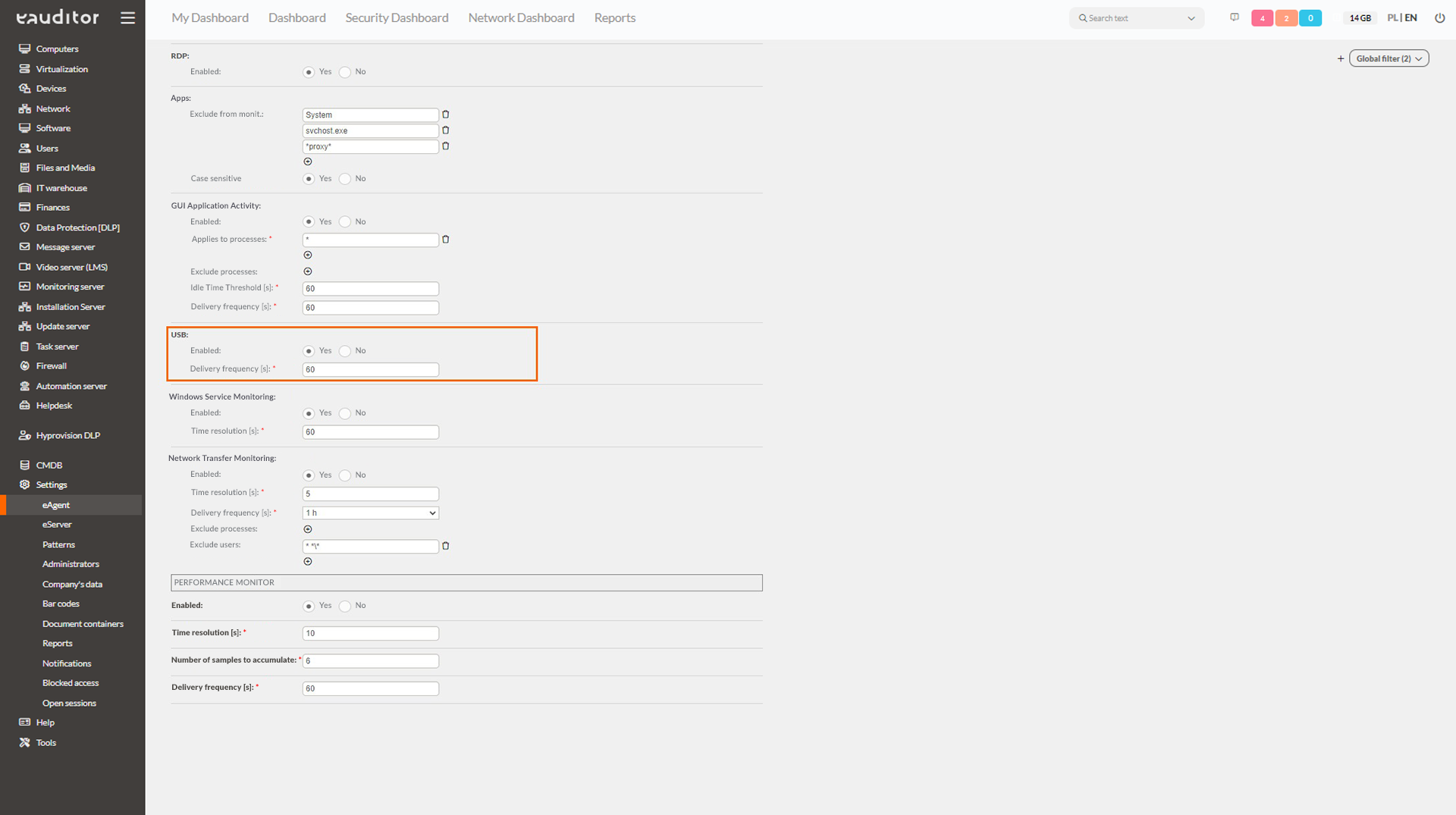
Step 1: Enable monitoring of USB devices
To do this, the administrator should go to the “Monitoring” tab in the eAgent configuration and confirm their desire to monitor all USB drives connected to computers, and define the frequency at which the connection information is sent to the system.
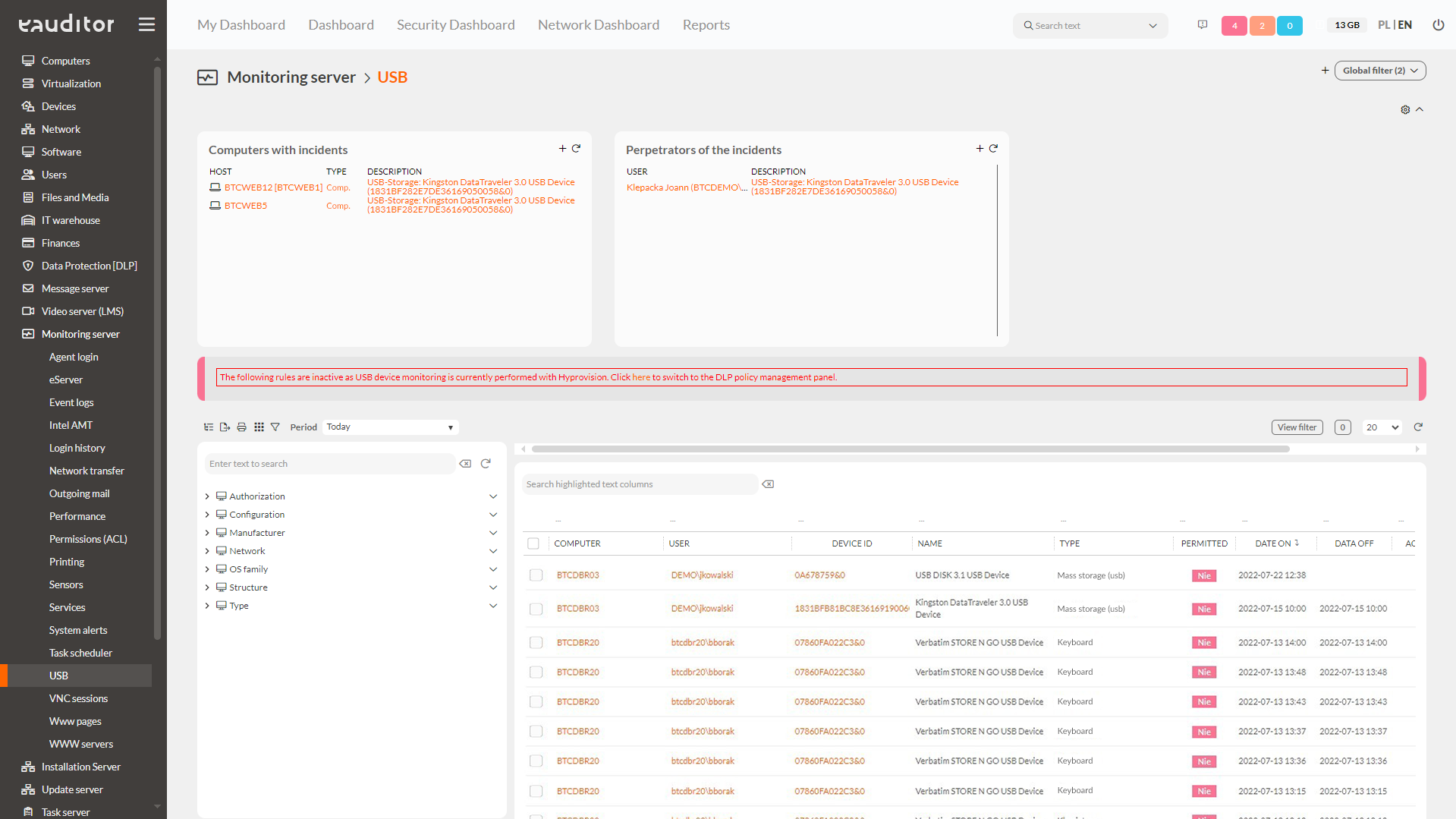
Step 2: Verify connected USB devices
In the Administration Console, go to the Monitoring Server > USB tab and verify that the system detects connected devices. In this view, it is also possible to check:
- USB device name,
- date of last use,
- the name of the computer on which the USB device was last used,
- the name of the user logged into the computer where the USB device was used,
- the presence of the USB device in question on the whitelist.
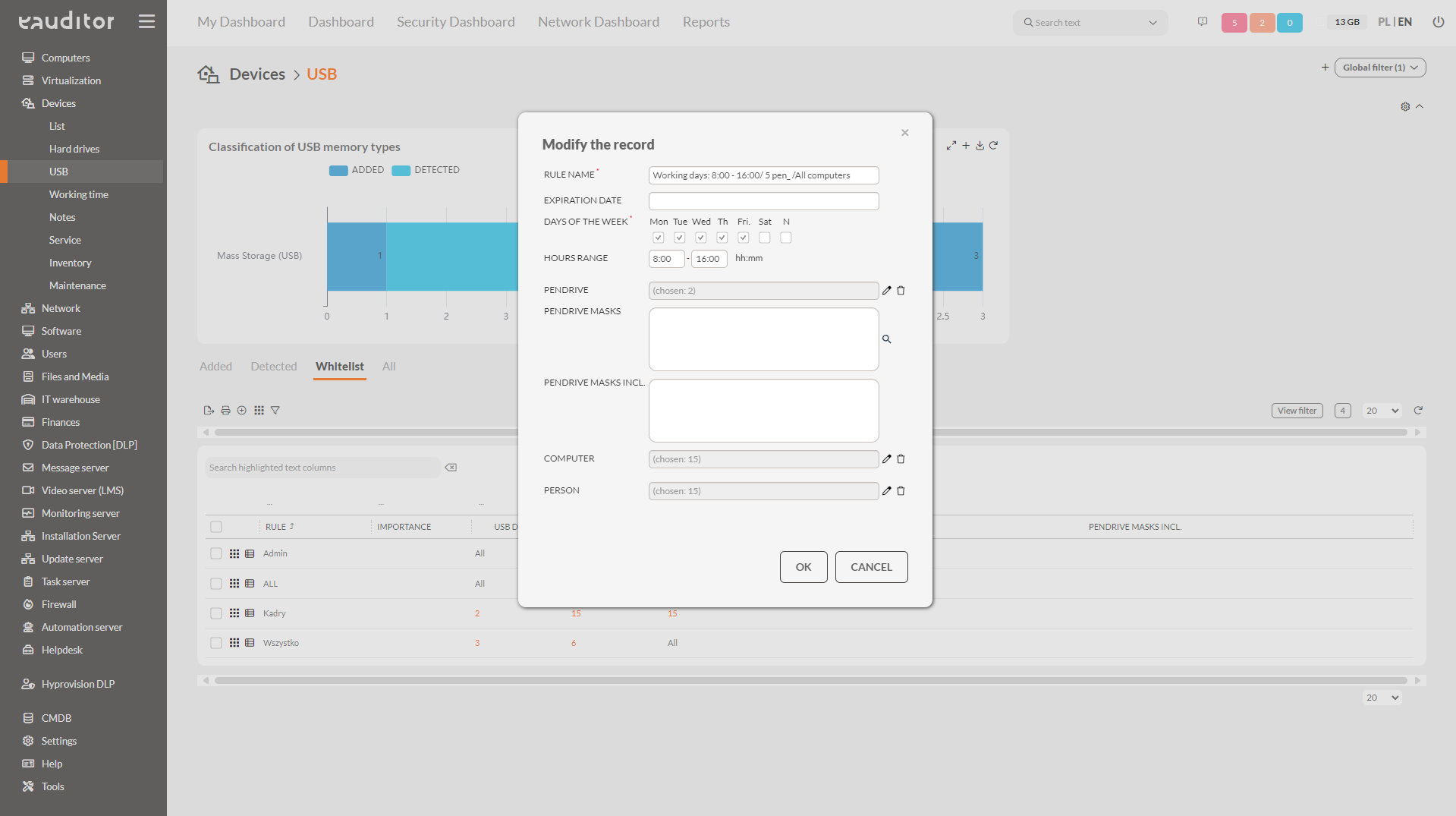
Step 3: Create a whitelist rule
The administrator, under Devices > USB > Whitelist, can define a rule that will prevent actions from being taken on connected USB devices that are not authorized by him. Considering the functioning of different organizational structures and security policies, eAuditor decided to make this option fully configurable. This allows the administrator to set the rule by defining:
- whitelist expiration date,
- days of the week and the range of hours in which it is valid,
- individual or all USB devices,
- flash drive masks (groups of flash drives covered by the policy – USB device names),
- computers on which the whitelist will run,
- users to whom the rule will apply during a login session.
Blocking USB drives with whitelisting – benefits
Saving time
The eAuditor system deliberately introduced a whitelisting policy, i.e. the ability to define authorized devices, which saves the administrator time. Therefore, the administrator in the system console, with a few clicks, can define only those devices he has verified and given to employees for use, and automatically block all others. In case the administrator would like to add an additional flash drive and authorize it, he can do so by listing it in the system.
Full flexibility in locking devices
Depending on the duties being carried out in the organization, each employee may have access to different data and different devices. To this end, it is necessary to provide the IT department with a flexible approach to locking USB drives to people in different organizational units or using different computers.
Grouping using masks
The ability to group USB drives using flash drive masks helps streamline and speed up whitelisting rules. All the administrator needs to do is give a specific name to the groups, which will enable him to block all USB devices marked with the same term.
Ability to generate cyclic reports
In the system, it is possible to simply report on the connection of flash drives defined in whitelists by employees in the organization. This gives the administrator an overview of who, when and on what device connected the allowed USB devices. In addition, the monitoring server allows the administrator to set a schedule for cyclic reports. This way, for example, every 30 days he will receive information about who has connected prohibited or allowed USB media during the desired period of time.
Any number of notifications
In addition, it is also possible to create any number of notifications in the system. They provide the administrator with information that a user has connected a prohibited USB device to the computer. The report is sent in any form via console alert, email or text message.
Informing an employee about an incident
Integration of the eAuditor system with Hyprovision DLP will enable the administrator to prepare a pop-up message that can be displayed to the user when an incident occurs. The content of the message is fully defined by the administrator. In addition, the incident generated by this unauthorized process is automatically logged in the system.