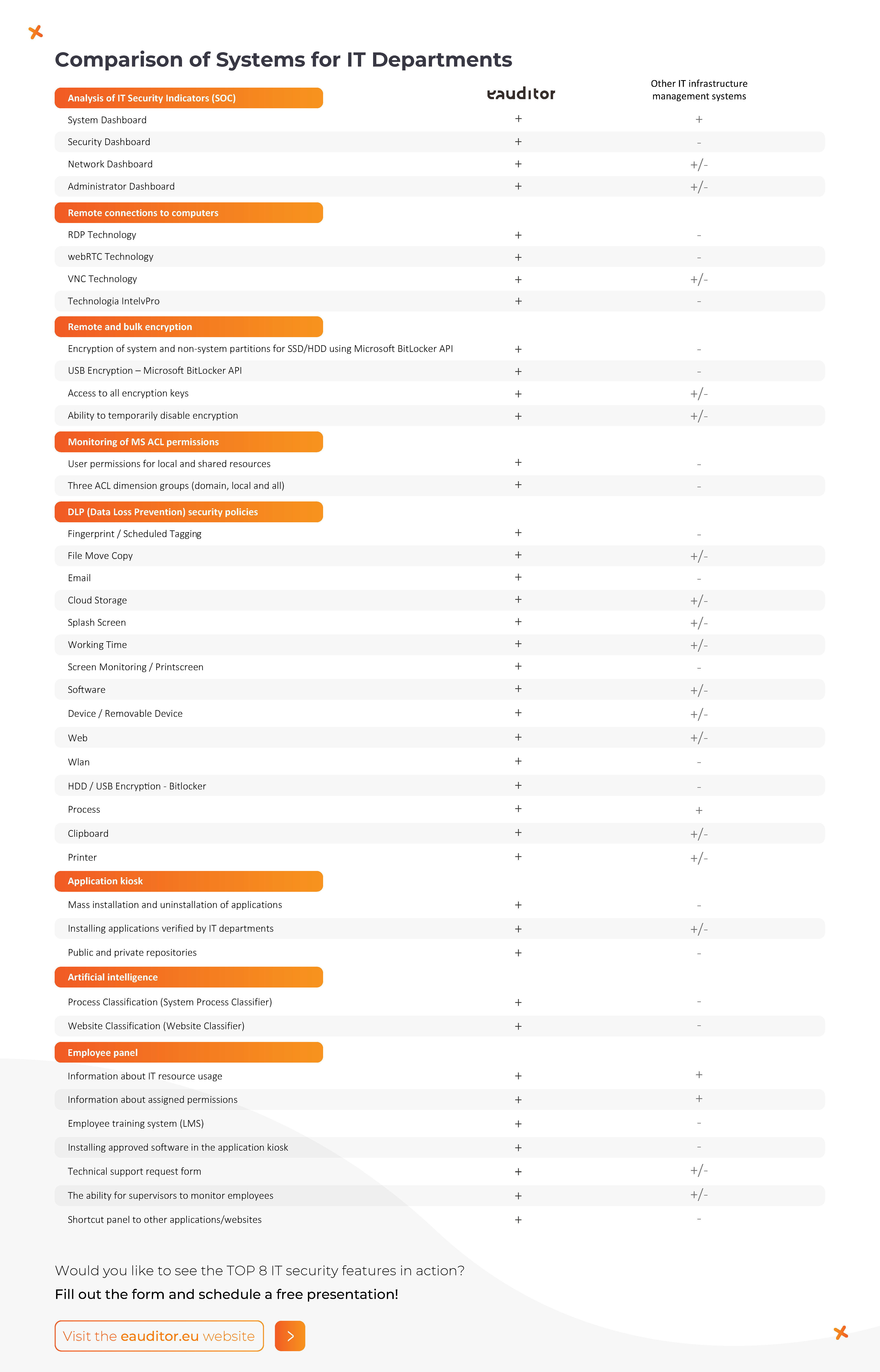
Top 8 functionalities for IT security
8 functions
to ensure data protection and incident prevention
19 DLP policies
To enhance IT security and protect against data leakage
1 system
to automation
and time savings for IT departments in organizations
The top 8 functionalities will work well for
What will you gain?
Data security
By implementing functionalities that enhance IT security, you are guaranteed that your customers’ data is protected from unauthorized access by outsiders.


Increase process efficiency
By ensuring proper IT security, you level the risk of incidents, thus preventing downtime for your organization.
Confidence that your image is under control
Implementing effective IT security software improves your organization’s reputation because by preventing cyber attacks, you increase trust among your customers.

Top 8 functionalities
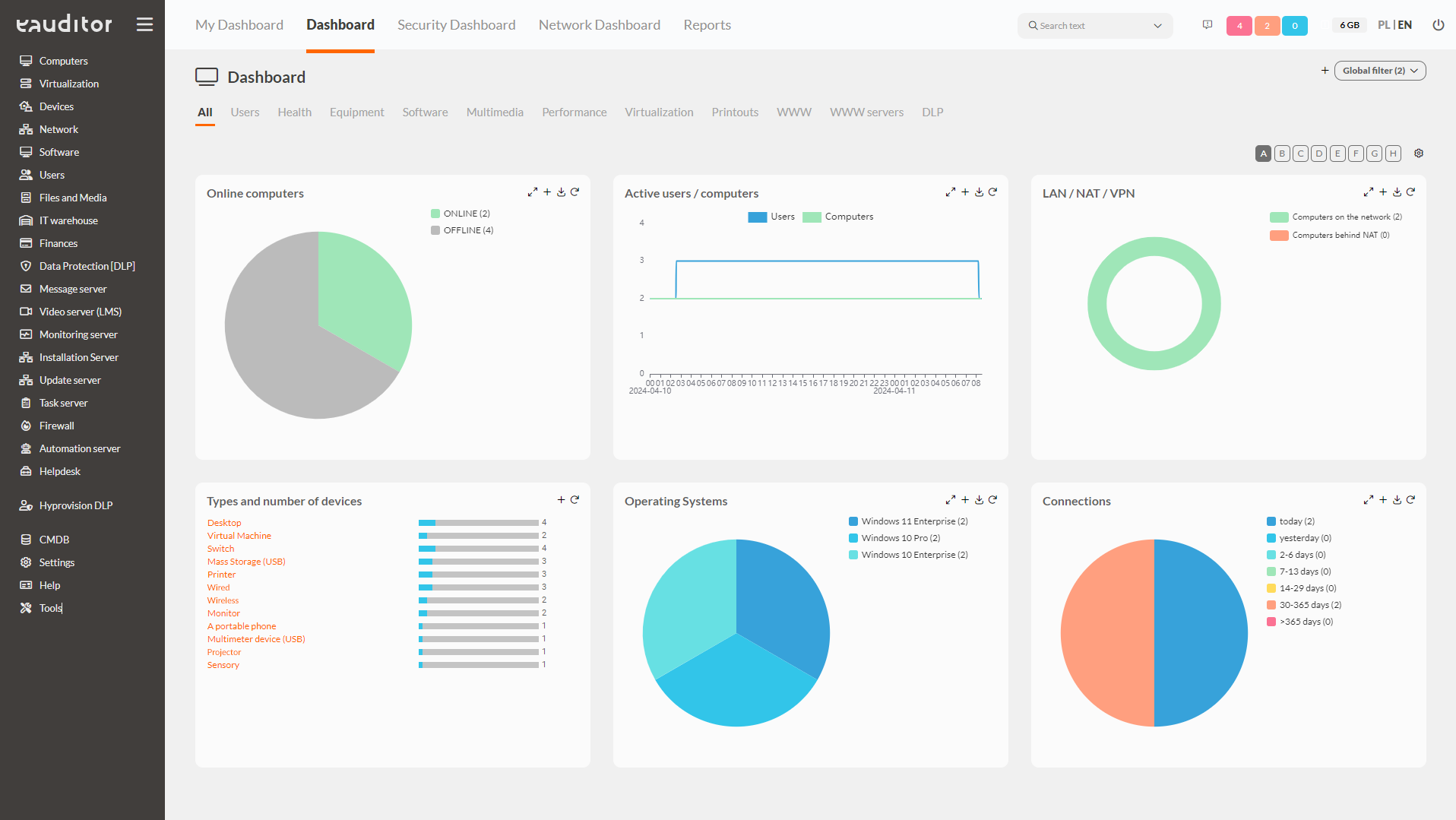
1. IT infrastructure security (SOC) indicators
It’s a functionality that allows you to view interactive widgets that present data on your IT infrastructure. This allows IT administrators to easily read information relevant to them regarding the status of IT resources in the organization, which will be immediately visible on interactive widgets. It also makes it possible to respond quickly in the event of any irregularities or disruptions to the infrastructure.
SYSTEM DASHBOARD | SECURITY DASHBOARD | NETWORK DASHBOARD | ADMIN DASHBOARD
2. secure remote connections to computers on the local network and behind NAT using RTC technology
Current work standards allow it to be done from anywhere. However, network connections to computers, both on the local network and outside the NAT, pose a serious risk. They are mainly caused by security gaps in the system, which can be exploited by cybercriminals. Therefore, it is important to provide users with confidence in the security of remote connections to workstations on the network.
RTC PROTOCOL (ON THE LOCAL NETWORK) | RTC PROTOCOL (OUTSIDE NAT)
3. use of artificial intelligence in the process of classifying websites based on the content (content) of the page
Manually classifying websites and checking their security is not only a time-consuming process, but also inefficient and unreliable. In order to make sure that verified sites are definitely secure, it is necessary to use proven and innovative functionalities in IT systems for this purpose. Using artificial intelligence, websites are automatically analyzed based on content, including for potential threats.
CERT BASE | URL HOUSE BASE | REGISTRY OF GAMBLING SITES
4. remote and mass encryption of system and non-system partitions for SSD/HDD and USB using MS BitLocker
Unencrypted disks are susceptible to access by unauthorized persons who can gain insight into important information related to the company’s operations. To protect them, it is recommended to implement a mass encryption solution for HDD/SSD drives and USB devices using Microsoft BitLocker. The technology allows for remote and automatic disk encryption, which effectively protects data from unauthorized access and enables secure storage of information in different environments.
MASSIVE AND REMOTE ENCRYPTION/DESCRYPTION of HDD/SSD and USB drives.
5. monitoring MS ACL permissions
In large organizations with several hundred employees, monitoring all the privileges granted to specific resources is not only difficult to do, but also risky. Assigning permissions manually can eventually lead to errors, allowing unauthorized people to access special category data. Lack of oversight of permissions also often leads to unknowingly losing information or damaging IT infrastructure. In the eAuditor system, the administrator can monitor user permissions to local and shared resources in real time by using a special API.
USER RIGHTS TO FOLDERS | FOLDERS SHARED WITH USERS
6. employee panel as an effective method of informing and training employees
In addition to the company’s key role of training employees on security policies, it is important to ensure that they have access to knowledge and tools to help maintain security compliance.
In the eAuditor system, the Employee Panel provides employees with insight into their productivity information, recent messages sent, support tickets, computer memory status
and available training. This allows you to easily and quickly manage your activities and tasks related to
With IT security.
MUTUAL COMMUNICATION | INFORMATION ABOUT USED EQUIPMENT | REPORTING MESSAGES TO IT
7. application kiosk as a method for employees to safely install software
Some applications installed by employees may contain malware, contributing to hacking attacks on the company’s network. This is why it is so important for companies to monitor the software installed by employees. The kiosk in the Employee Panel is a guarantee that all installations made by employed
people in the company have been verified and then approved by IT departments. In addition, the uploading of applications to the repository and the downloading of them by employees is done using SSL, which guarantees a high level of security. As an additional convenience for administrators, the eAuditor system also automatically notifies them not only if the software required by a department is not installed, but also if it is not used at work.
BULK INSTALLATION AND UNINSTALLATION | SOFTWARE AND APPLICATION UPDATES
8. selected DLP security policies in practice
Today, many organizations from different economic sectors are increasingly vulnerable to attacks by cybercriminals. Hackers are also becoming more efficient in their operations. Specific DLP (Data Loss Prevention) security policies allow to monitor and control the transmission of special category data in the organization, thus protecting against cyber attacks. With powerful functionalities, they also enable detection and blocking of data leakage attempts, covering sent emails, documents and files uploaded to cloud applications.
DLP policies for comprehensive data leakage protection:
FINGERPRINT | SCHEDULED TAGGING | FILE MOVE COPY | EMAIL | CLOUD STORAGE