Network monitoring
- Network Scanner
- Network Maps
- Monitoring Network Devices
- Monitoring Network Infrastructure Integrity
Table of contents
What is network monitoring?
It is a process that is carried out through the network scanner in the eAuditor system. Its operation involves searching a computer network to find all connected devices that have an IP address that falls within the address range set during the scanner’s configuration.
How does the network scanner work?
The scanner is based on the ICMP protocol. Thanks to it, such programs work as:
- ping – checks whether a connection has occurred,
- tracert – checks the route and what devices the packet passes through.
The network scanner uses an “ICMP Echo Request” message sent from the scanner to the host, to which the host must respond. This is a designated address from the range set during scanner configuration. If the host does not respond with an “ICMP Echo Reply” message, the scanner then checks the active ports.
Functions within the network scanner
Functions within the network scanner
- network scanning,
- eAgent installations,
- adding devices to the inventory,
- monitoring of network devices (SNMP),
- port/service monitoring.
Scanning the network
1 To scan the network, select:
- ports (services)
- IP address range
- approve or reject the scan via SNMP as well.
2 Set automatic scanning (according to the schedule). To set the schedule, select:
- frequency,
- the start date of the schedule,
- schedule start time.
Remote installation of the agent
To install the agent remotely, use the “Install eAgent remotely” option. The scanner has the ability to install it in the eAuditor / Hyprovision system on computers connected to the network and having a supported operating system. Before remote installation, it is required to configure the computer properly. The scanner allows installation of any software on computers (including those not equipped with an agent). To install software on computers in the local network, two conditions must be met:
- the application must be in a repository on the server (it is possible to add any application to the repository),
- the computer must have the right system and the right configuration.
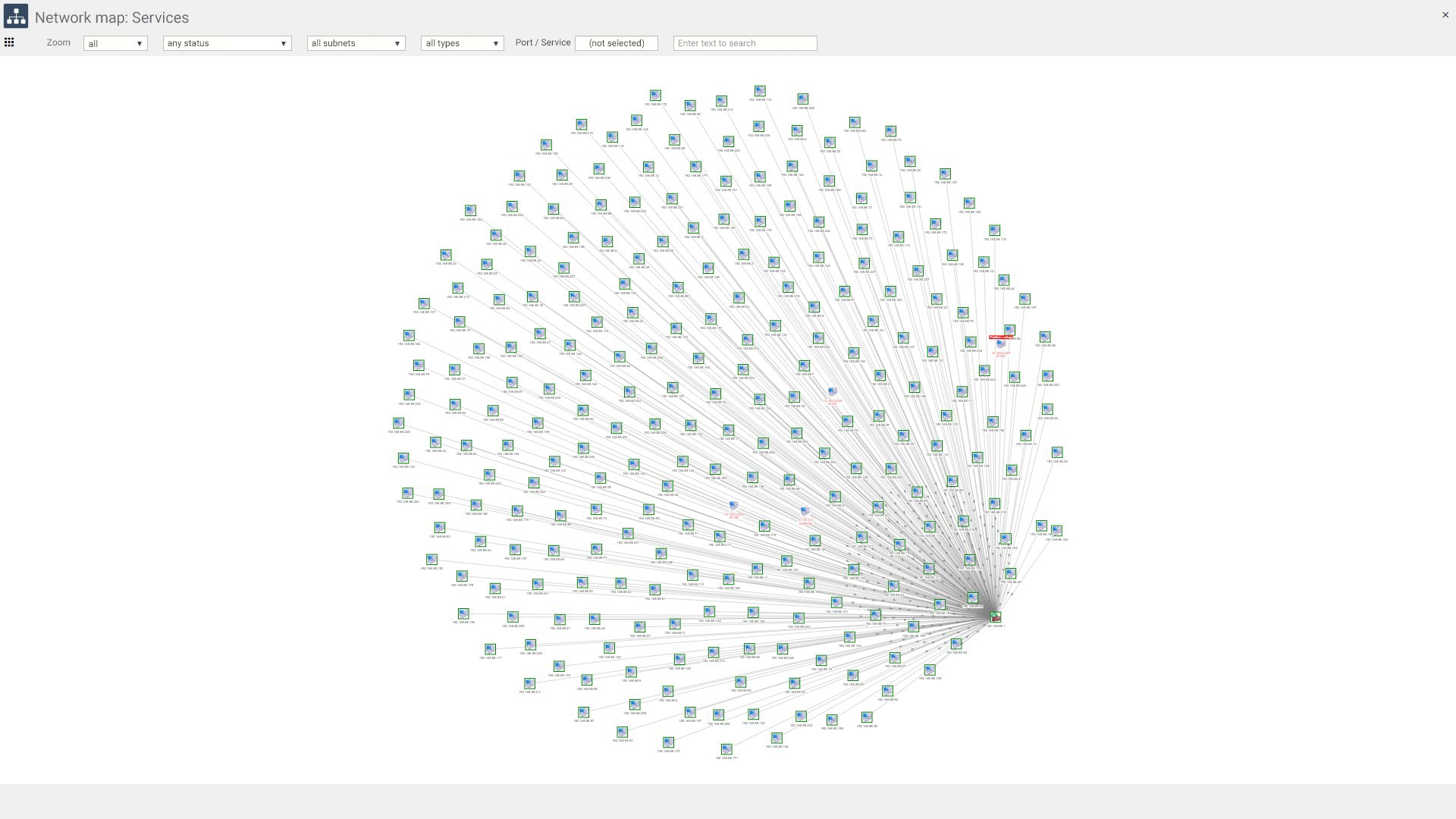
Reading network maps
Monitoring connections between networks in an organization, is possible thanks to the network map available in the system. It allows you to obtain detailed information about a given network. This map works on the basis of data coming from the network scanner. It depicts in graphical form the network connections between any devices such as printers or computers. There are 8 dedicated maps built into the eAuditor system:
- no problems (devices with no service issues),
- printers,
- offline computers,
- online computers,
- problems (devices with a service problem),
- switche,
- services.
The view is fully customizable and filterable. It is possible to indicate the status of devices and show only those that are online or offline.
In addition, within the view, the administrator can filter also:
- selected subnets,
- device types (printer, computer, router, switch, VoIP phone, n/a),
- port and service name,
- device status (offline, online or any),
- zoom (from 20% to 400%),
- any phrase to search for.
Reading network maps allows you to quickly identify devices that are not functioning properly and manifesting some kind of malfunction such as a service problem. The system therefore allows you to define your own network maps and filter them according to your preferences.
Monitoring of network devices
With the appropriate system configuration, it is possible to monitor devices and ports on a specific network. Any irregularities occurring within the monitored devices can result in automatic notifications to the IT administrator. In the system, it is possible to scan a specific device along with an indication of its type, date and status. If everything runs correctly, the administrator is informed that no failures were detected during the scan or indicates specific defects. In addition, scanning in the system can be done in 3 ways: manually, using a schedule or using DHCP requests. In addition, the eAuditor system also enables scanning of ports used by computers, so it is possible to monitor services that use particular devices in the organization. Network device monitoring enables support for the SNMP protocol, making it possible to check, among other things, information about devices such as switches and ports – identifying which are free and which are busy, etc. Monitoring of network devices therefore allows streamlining the process of recording IT resources and responding to faults as they arise. It also identifies new devices connected to the network.
Monitoring the correctness of the network infrastructure
Each service in the eAuditor system uses a specific port to communicate on the network. By scanning active ports, you can determine which services are active and which are not. If they are inactive, a prompt will appear in the console informing you of problems with a particular service. In addition, for convenience, the port then will be marked in red. On the other hand, a service that is functioning properly will be marked in green. There is also an available predefined list of services by category, service and port. In addition, everything that is sent to the computer network requires the use of a computer port for data transmission. This means that the system also makes it possible to monitor infrastructure resources such as ports on which computer applications, instant messaging or peer to peer applications run, among others. This allows the system to inventory IT equipment, as the scanner transmits information about IP addresses and network adapters (MACs). In addition, the scanner of the eAuditor system collects information about the quality of the connection taking into account the response time of services (services) given in milliseconds and the amount of information delivered (number of packets delivered, lost and percentage of losses). The monitoring of IT resources in the eAuditor system therefore translates into the correctness of the network infrastructure. This preserves IT security in the organization and prevents network failures.
Benefits
Want to learn more about this functionality? Read our article “IT network monitoring – running your business safely”.