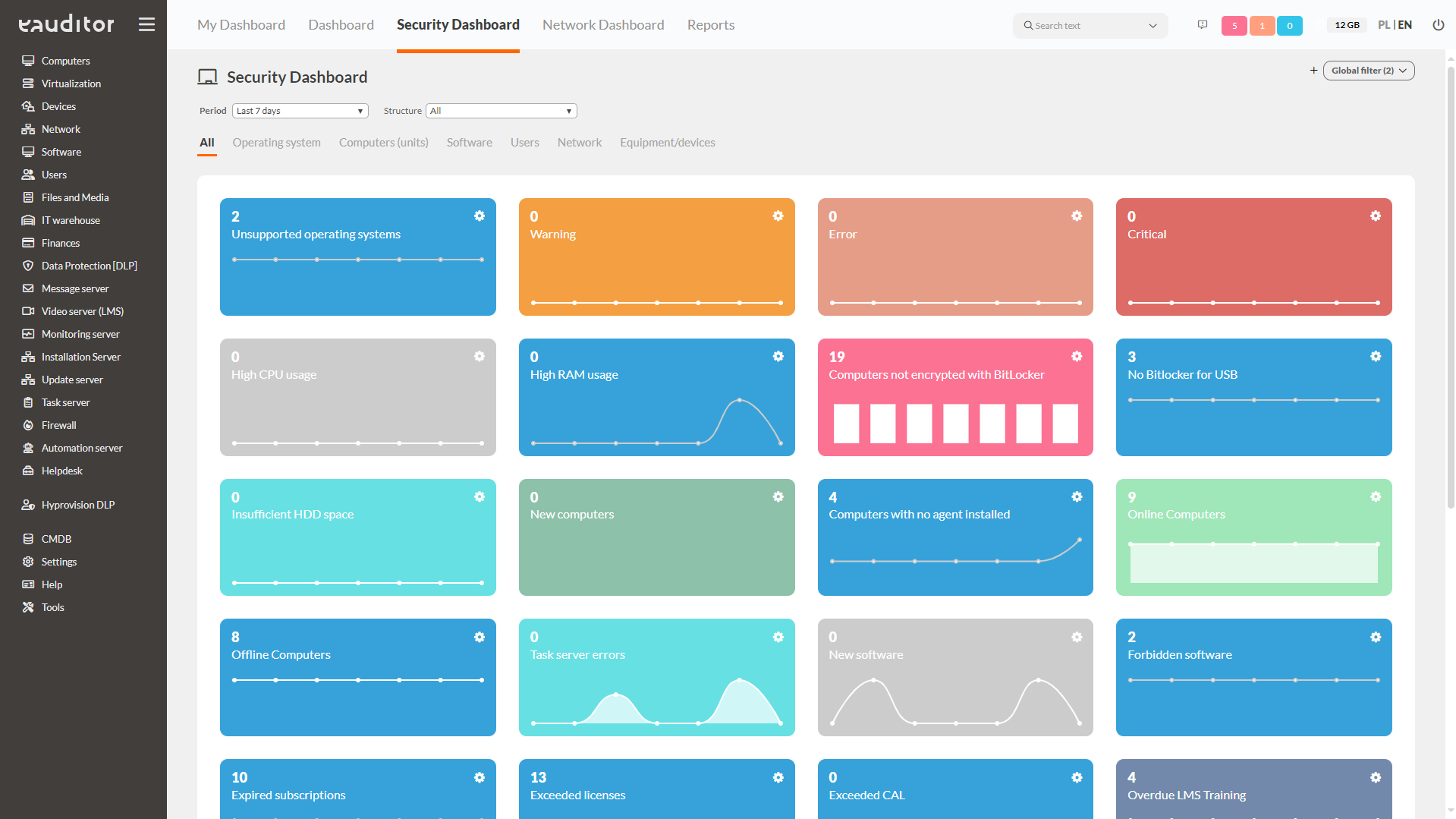
IT security
- Analysis of key SOC indicators
- Remote BitLocker encryption
- Blocking access to websites and processes
- USB blocking
- Application blocking
- Two-factor authentication
Table of contents
What is IT security?
IT security is closely related to the estimation and control of emerging risks and threats in an organization. It is a set of issues related to guaranteeing consistency, confidentiality and security in the circulation of information in IT systems. This makes it possible to verify installed systems and equipment for compliance with specifications and applicable laws. In addition, comprehensive protection of IT infrastructure and activities undertaken by employees affects the security of key resources, including data.
Components
IT security includes activities related to the protection of data stored on all devices in an organization. This is one of the key processes implemented by IT departments, as data leakage can cause serious consequences and disrupt the continuity of business processes. In addition, protection also applies to running processes and visited websites preventing from, for example, pishing. The most important elements of implementing this process should be identified as: