Inventory of computers and servers
- Automatic Inventory of Computers on the Local Network and beyond NAT
- Importing Computers from Active Directory
- Verification of Virtual Machines Assigned to the Serverntent Goes Here
Table of contents
Inventory of computers and servers
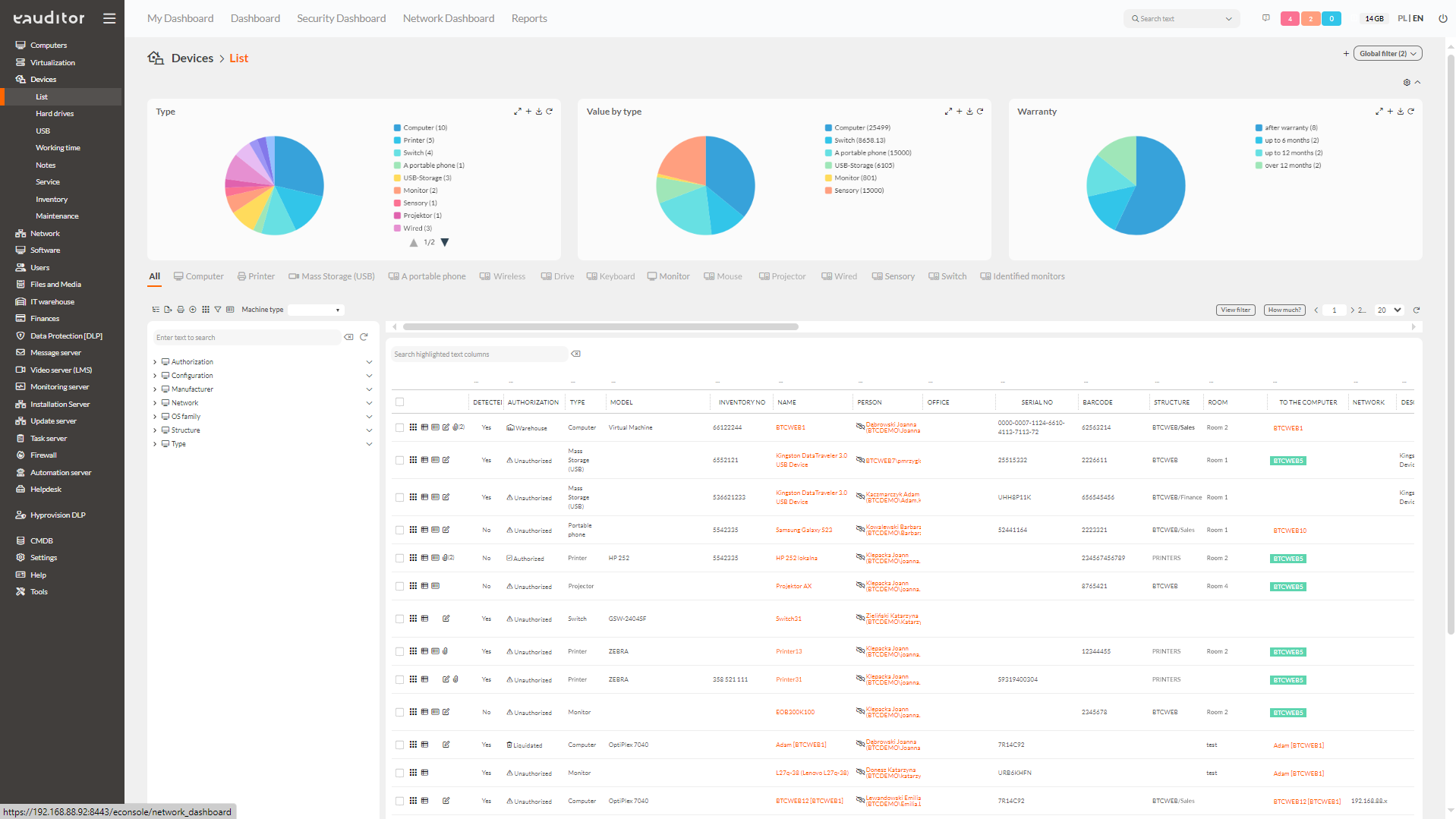
Computer inventory
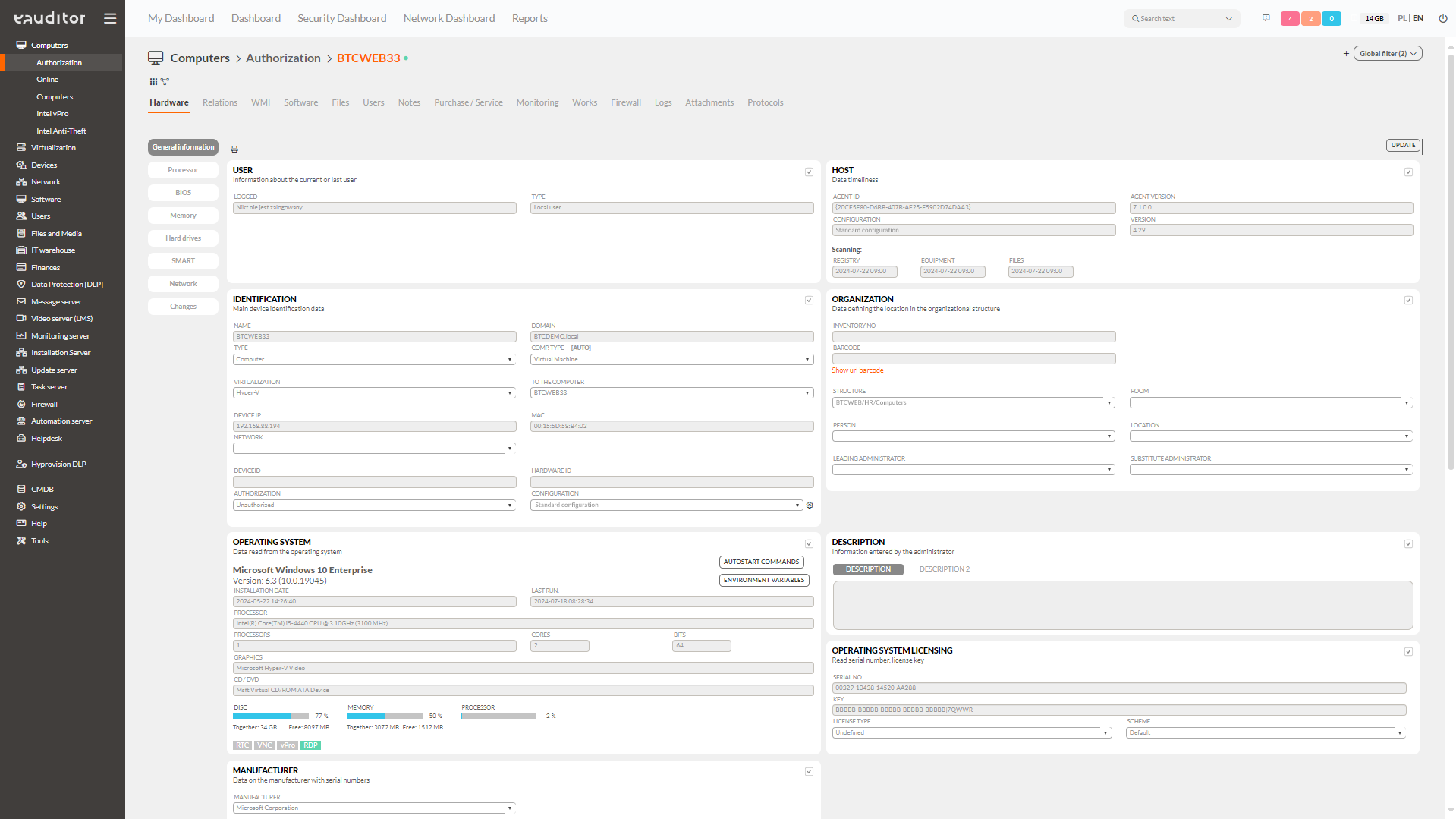
The eAuditor system allows you to conduct an automatic inventory of computers that are located on the local network and outside it (behind NAT). As part of this feature, the IT administrator has access to the detail sheet of a given computer, containing a range of key information such as:
- Information about the current or last user,
- Timeliness of eAgent data and scanning,
- The main identification data of the device,
- Information specifying the location of equipment in the organizational structure,
- Data read from the operating system including serial number, license key,
- Equipment manufacturer data with serial numbers,
- Entered service information,
- Registered and generated documents: handover protocol, return protocol.
At the time of system implementation, it is possible to simply and quickly import all computers in the organization, for example, from Active Directory or other sources. For inventory purposes, it is possible to assign a given computer to:
- specific organizational structure,
- the exact location and the room in which it is located,
- person assigned under the transfer protocol,
- lead administrator.
For computer inventory, it is also possible to download dozens of predefined reports for most views related to the computer detail sheet. This makes it possible to create statements in popular .xls, .csv, .pdf formats, but also to print them out in paper form. The built-in report scheduler also allows you to send reports by e-mail according to a specified frequency.
Server inventory
In the eAuditor system, it is possible to maintain an inventory of the organization’s owned servers. Thanks to this, in one panel, the administrator will receive information regarding:
- server names,
- CPU,
- memory (available on the server and disks, current usage),
- network card,
- installed system,
- launch dates.
In addition, it is possible to check the virtual machines assigned to a given server. We write more about virtual machine inventory here. We write more about virtual machine inventory here.