Software inventory
- Inventory of applications and packages
- Software inventory
Table of contents
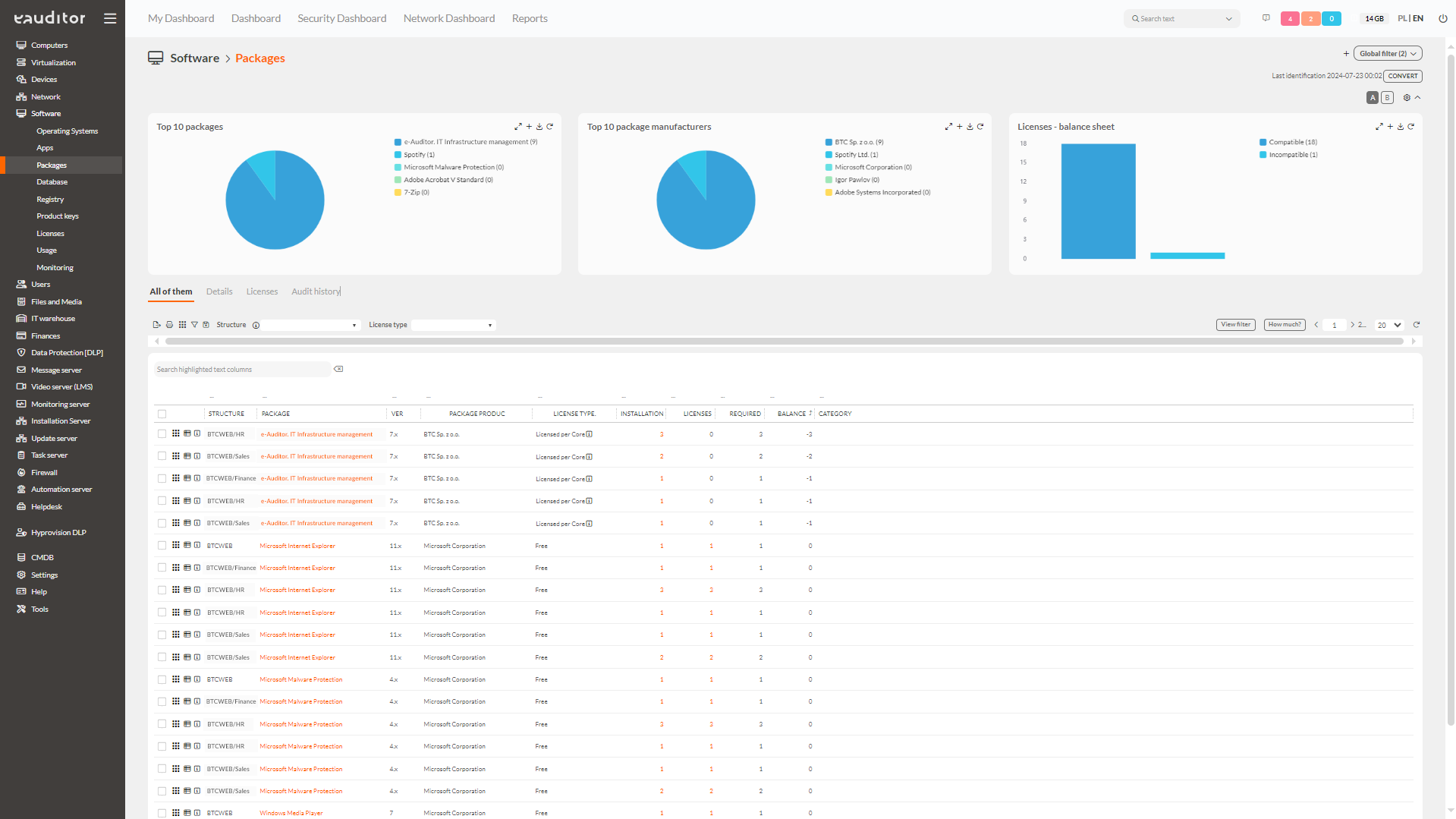
Inventory of applications and packages
In the eAuditor system, it is possible to carry out an inventory of software that is installed on computers. The administrator gets to see a detailed list containing information on:
- the name of the application / package,
- version used,
- the manufacturer of the application / package,
- license type,
- number of installations,
- application / package category.
It is possible for the administrator to specify whether an application / package is prohibited, recommended, additional or unspecified. This allows you to quickly obtain a list of applications, e.g. recommended ones, along with an indication of computers.
Packages in the eAuditor system are grouped applications due to a variable specified in the system or manufacturer. An example of a package is the MS Office suite within which applications such as Word, Excel, PowerPoint, etc. are available.
Identification of software for inventory purposes is done in a dual way, thus ensuring high efficiency of application/package detection. This method consists in juxtaposing the variables: registry entry and executable file (*.exe) with the application/package pattern.
Pattern databases
Reading installed applications and packages involves matching the detected software with its counterpart in the pattern database. In order to maintain a high level of accuracy, pattern databases should be updated on an ongoing basis. Two types of pattern bases are available in the eAuditor system:
Public database of patterns
The public database of patterns is updated on a regular basis as part of automatic updates to the eAuditor system. This database contains a broad catalog of well-known applications and software packages that are regularly updated by the system’s vendors. Thus, administrators are assured that the latest versions of popular software are always recognized and correctly classified. The public pattern database is ideal for organizations that want to minimize the workload associated with manual management of software patterns.
Private pattern database
Created individually by the organization’s administrator. When it is activated, the system will prioritize the parameters set in it, which means that software matching will first be checked against the private pattern database before checking against the public database. The private pattern database allows organizations to customize software recognition to meet specific needs and requirements, including proprietary software or rare applications that may not be present in the public database. Administrators can add, delete and modify entries in the private pattern database, ensuring that all applications used in the organization are properly recognized and managed.
Updating of the pattern database is fully automatic.