IAM management
- Access automation
- Control of entitlements
- Central access management
- Audit of entitlements
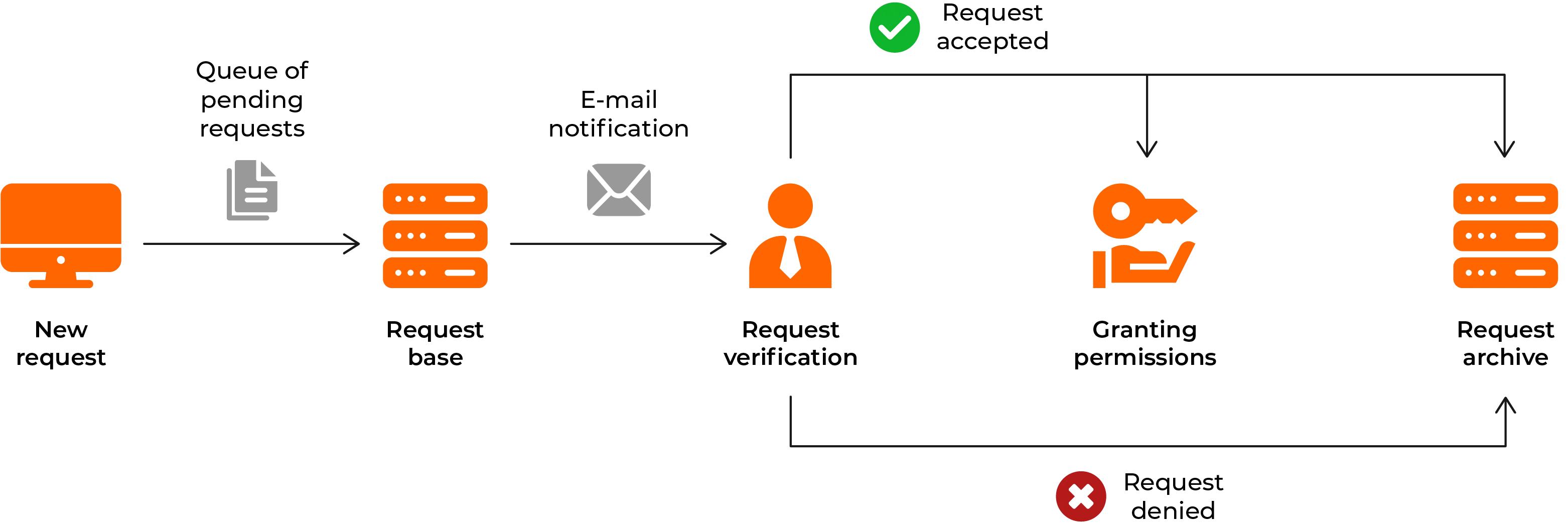
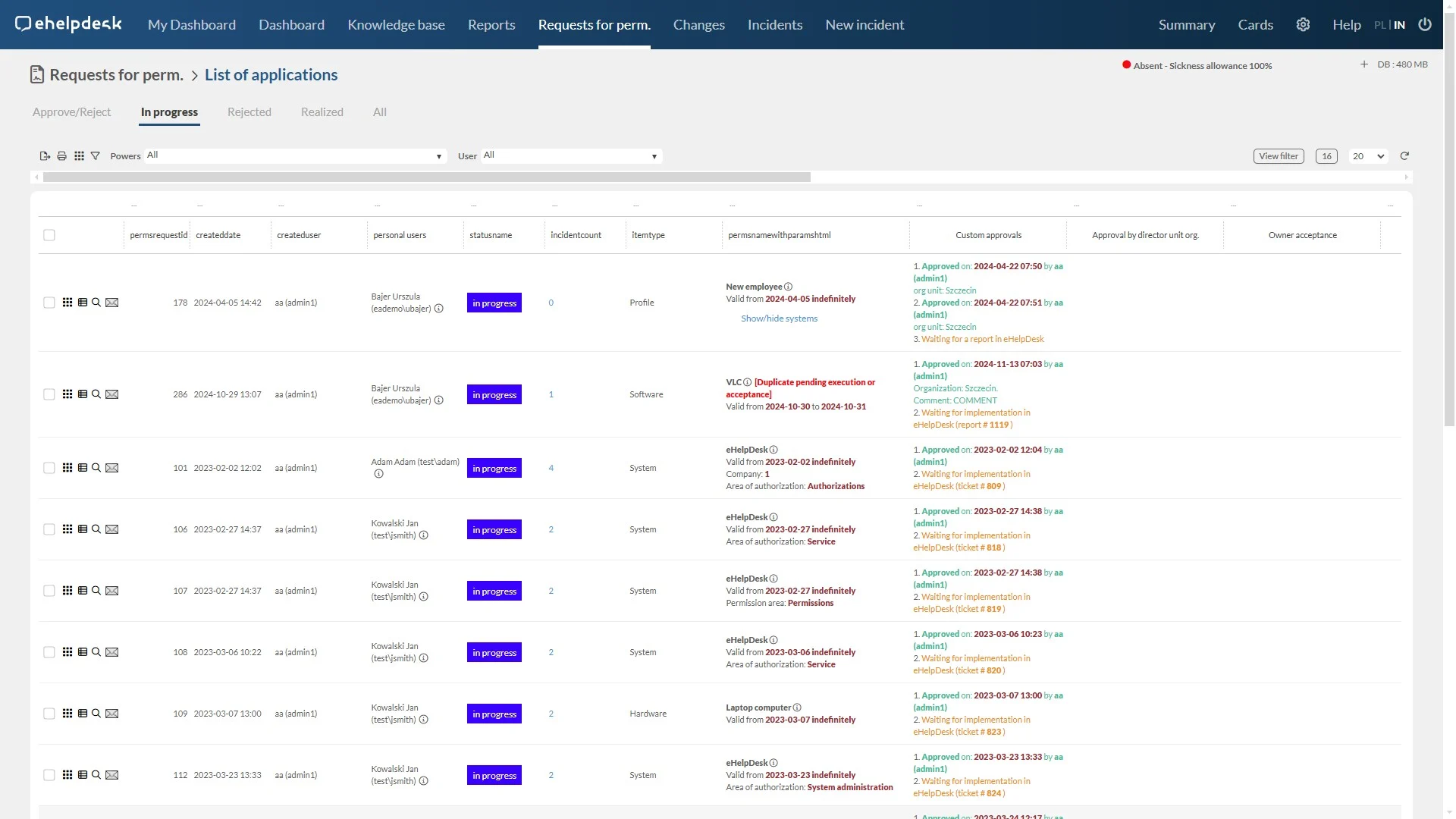
Creating an entitlement request
The new privilege request functionality allows users to easily and quickly request additional privileges or access to new resources.
-
Simple process: An intuitive form and automatic redirection of the request to the appropriate people make the process quick and easy for users.
-
Status tracking: Users can monitor the status of their application in real time, increasing transparency and reducing the need for manual tracking.
-
Reduction of errors: The electronic application process minimizes the risk of errors, such as omitting important information or sending the application to the wrong person.
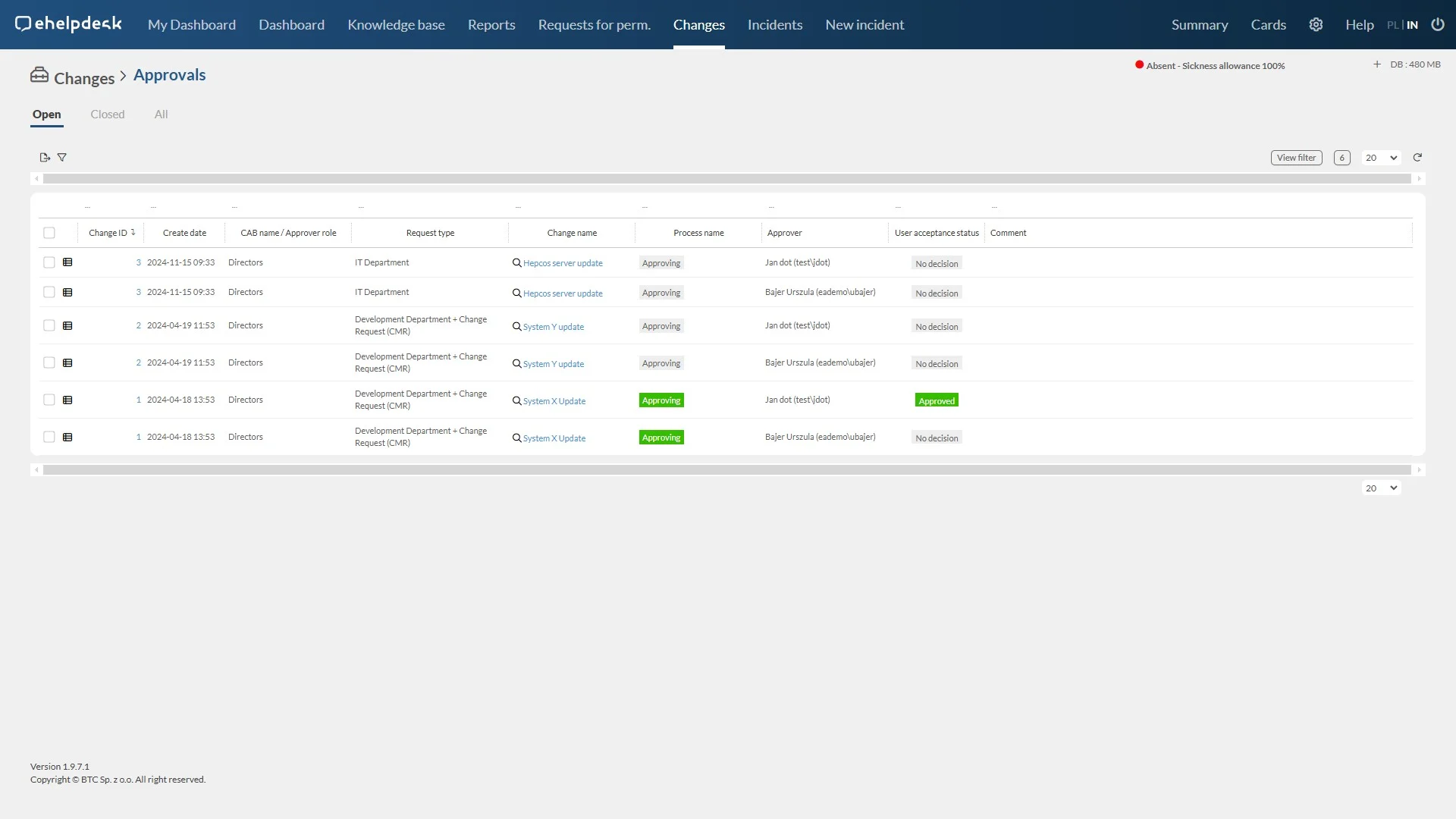
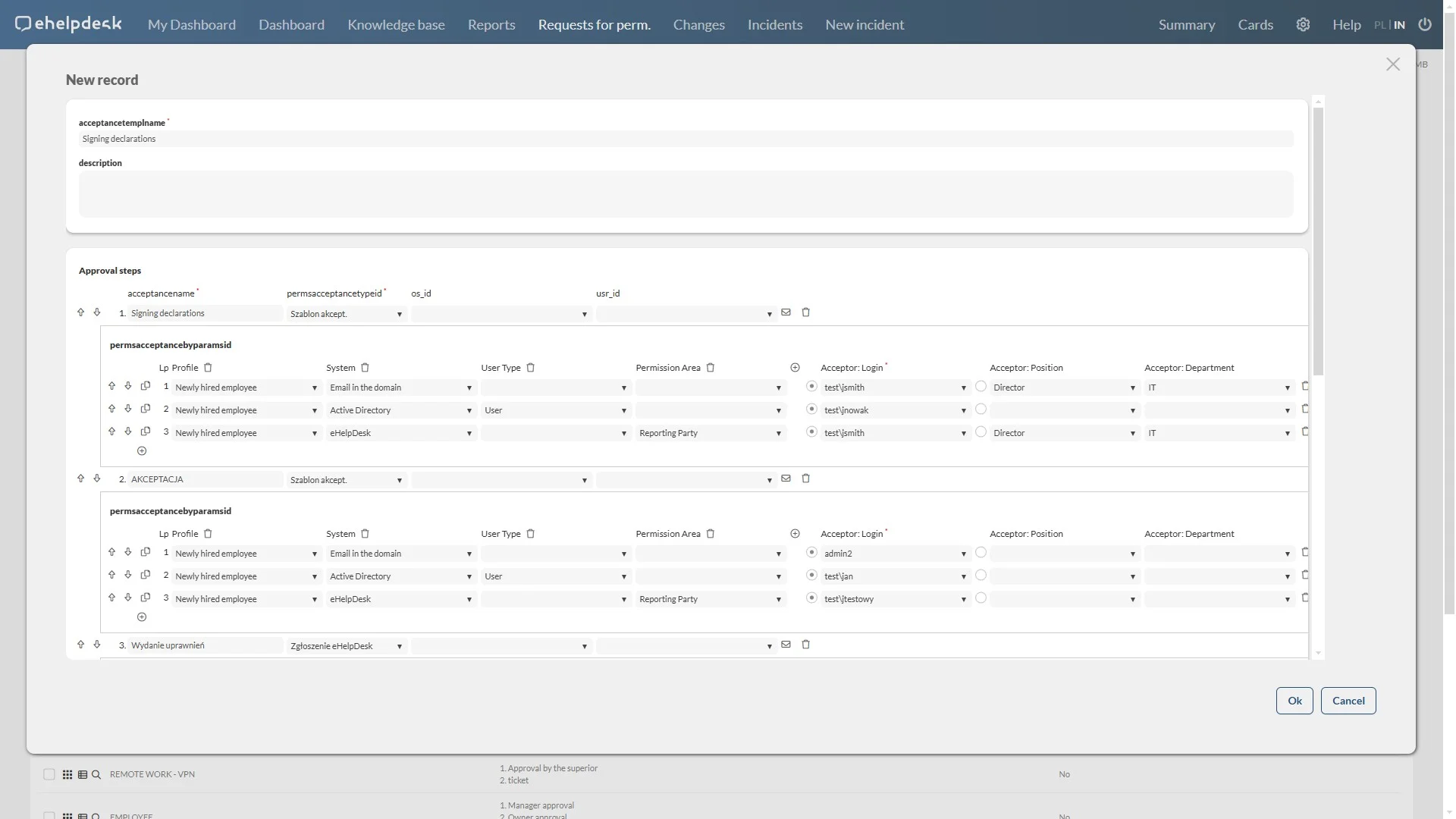
Acceptance of rights
The authorization request acceptance functionality enables decision makers to process authorization requests from users quickly and efficiently.
-
Efficiency: Centralized request management enables rapid decision-making, which speeds up the authorization process.
-
Policy compliance: Functionality supports compliance of decisions with company policies, which minimizes the risk of granting inappropriate authorizations.
-
Security: By thoroughly vetting applications, decision makers can ensure that permissions are granted only to users who actually need them.
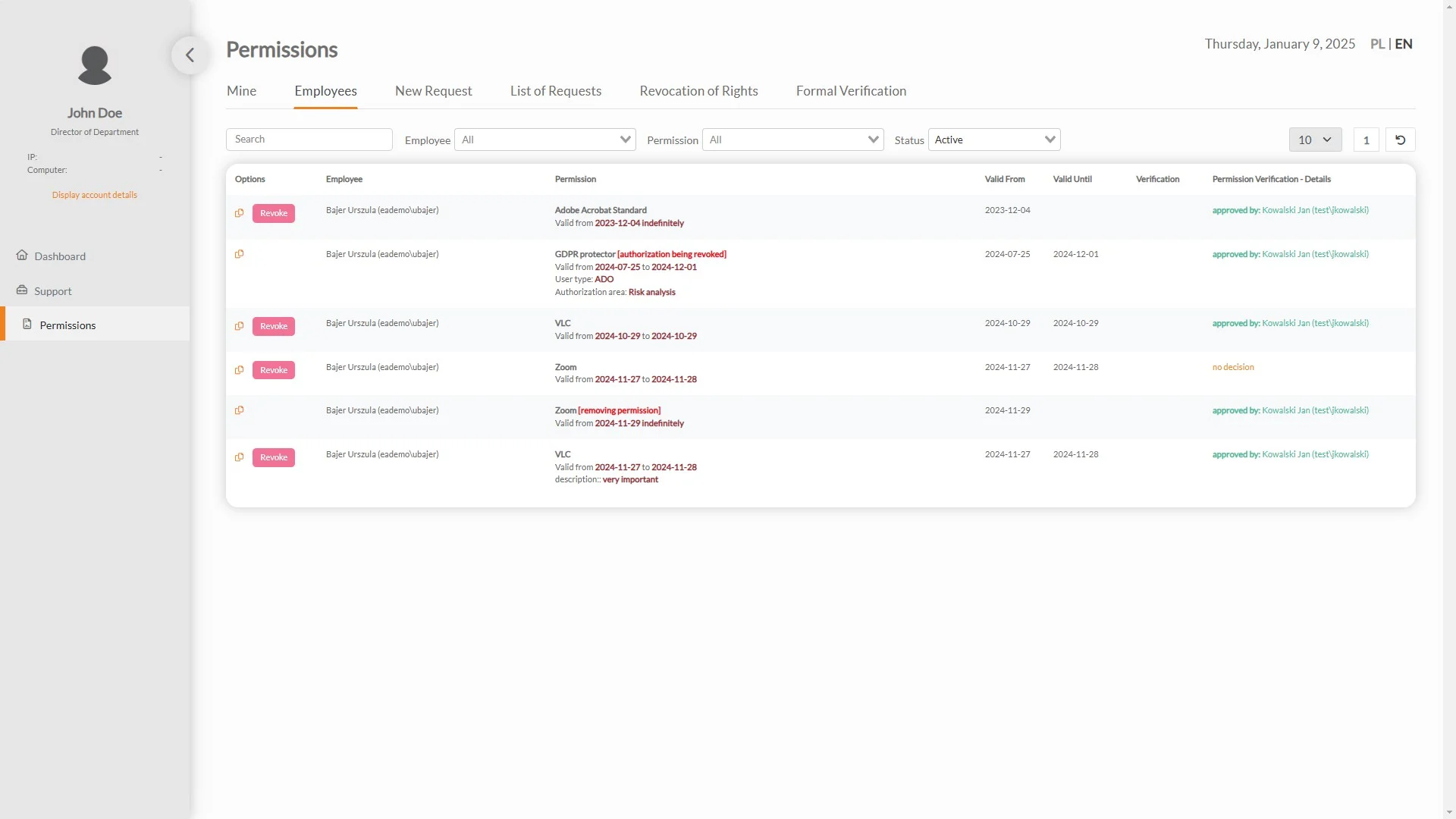
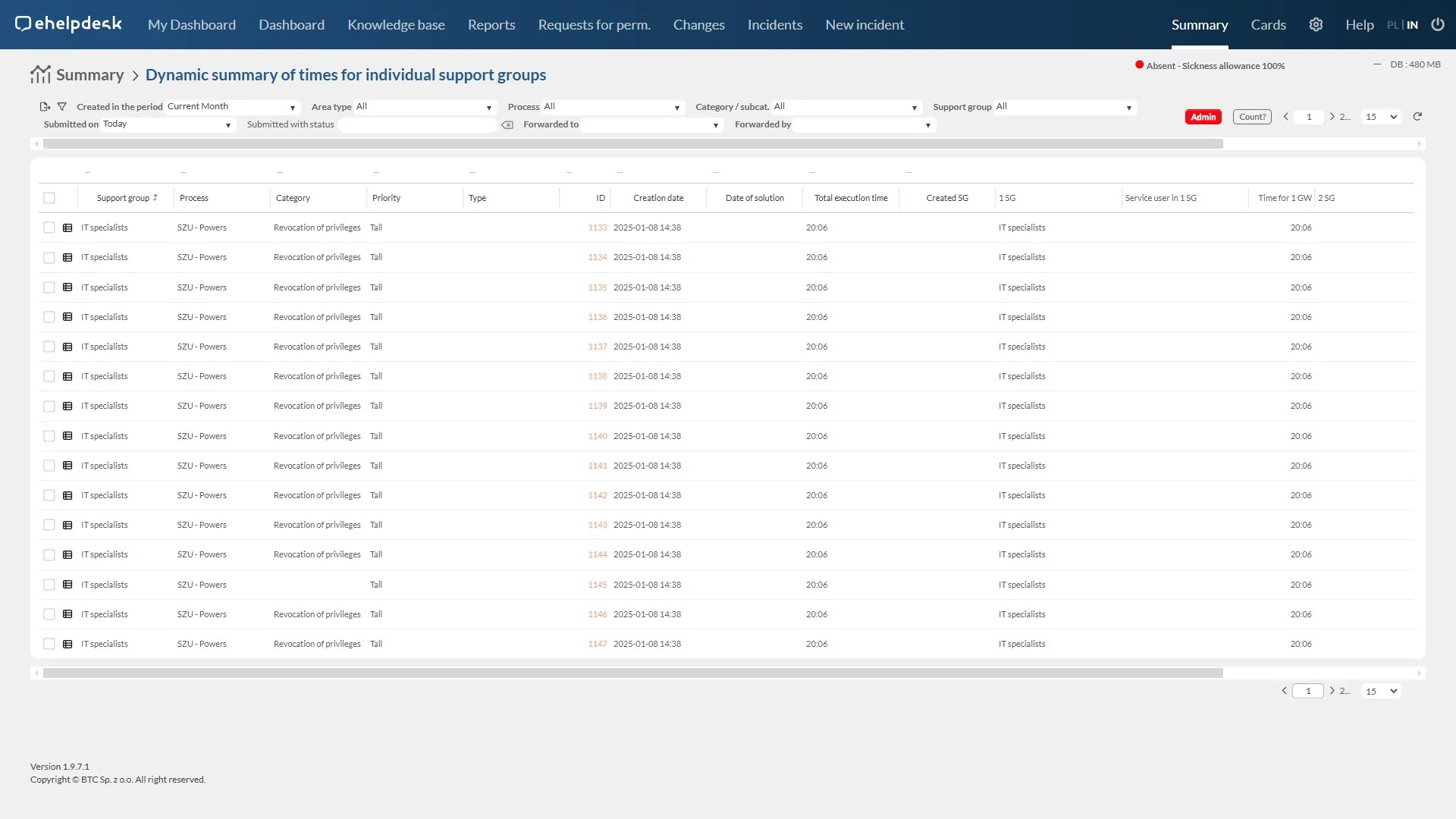
Audit of entitlements
The privilege verification functionality allows you to check and confirm whether system users have the appropriate privileges to perform certain actions or access resources.
-
Enhanced security: Regular authorization verification helps identify and eliminate unauthorized access, strengthening the protection of company data and resources.
-
Fraud Prevention: Early detection and correction of incorrect authorizations minimizes the risk of fraud and unauthorized activities.
-
Accurate reports: The system generates verification reports, allowing you to monitor compliance and analyze entitlement risks.
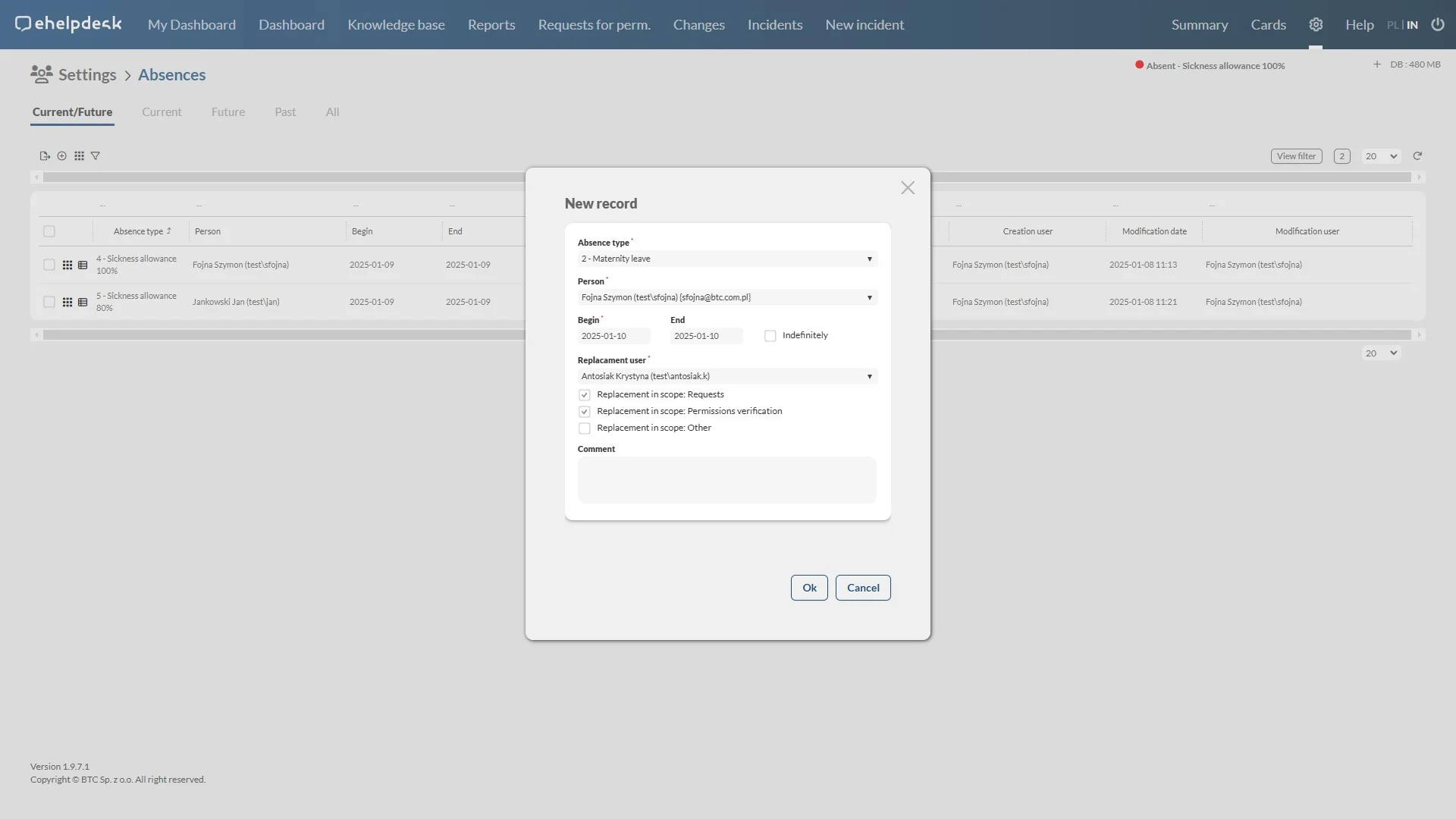
Absences/replacements
Comprehensive handling of vacation requests, sick leave and other forms of employee absences.
-
Streamlining processes: Automating the submission and processing of absence requests reduces administrative work and minimizes the risk of errors.
-
Easy access to the archive: Absence history is easily accessible, making it easier to conduct audits and manage employee data.
-
Better planning: With a central system, managers can better plan human resources, resulting in greater team efficiency.
Table of contents
How does the entitlement request processing work?