NIS2 #6: Remote Installation
Remote software installation in accordance with NIS2 guidelines
NIS2 in a nutshell
Did you know that the new NIS2 directive no longer applies only to IT infrastructure managers, but also covers entire supply chains, imposing obligations on all companies critical to the economy. Does your entity work with suppliers or business partners? If so, you need to understand how the new regulations may affect your business relationships and data protection obligations. In this email, we’ll discuss how NIS2 affects supply chain security and what you can do to ensure compliance with the new regulations.
Security in the supply chain – what does NIS2 change?
NIS2 requires that entities not only protect their own IT systems, but also ensure cyber security compliance at all stages of the supply chain. This means regularly analyzing the risks associated with suppliers and third parties, as well as putting safeguards in place at every stage of the relationship. Failure to comply with these requirements can lead to serious financial consequences and even block access to key business partners.
How to meet NIS2 requirements with eAuditor IAM?
Remote installation
USE CASE
In connection with the implementation of the NIS2 directive provisions in the unit, it has become necessary to control the applications used by users. The provisions of the NIS2 Directive stipulate the need to ensure that the applications used in the unit on all end machines meet the security and expediency requirements of the institution. The functionality of the Application Kiosk responds to the requirements of Article 21 by eliminating the risks arising from unauthorized software. The unit therefore decided to use the eAuditor system to force the installation of desired applications in the latest versions.
- A system agent was installed on the computers.
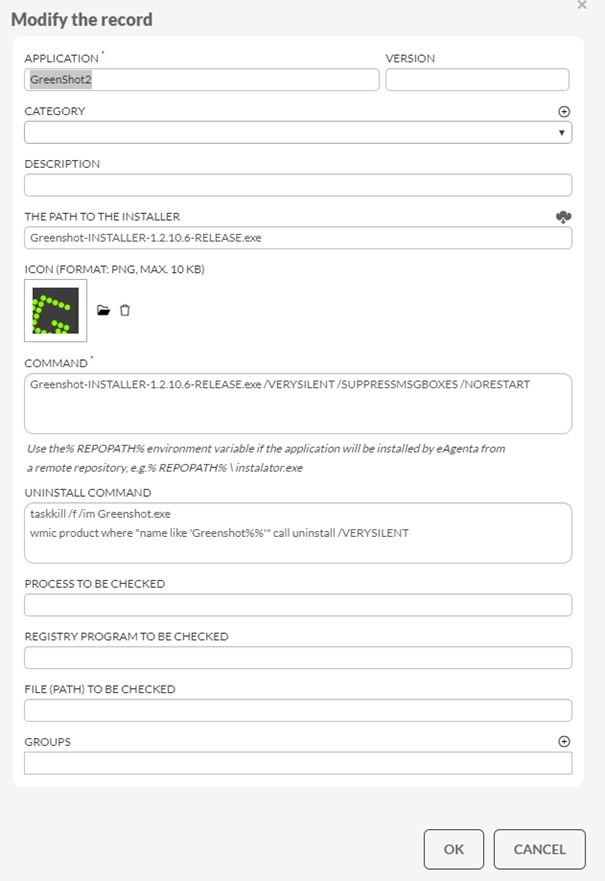
- Remote installation packages in the eAuditor system were prepared and established in the remote installation server.They started by preparing installation packages for the desired applications while setting up the processes and files to be checked.
This will allow the system to see on which machines the software should be automatically installed.
Remote installation packages were then created and distributed, creating groups of the desired software.
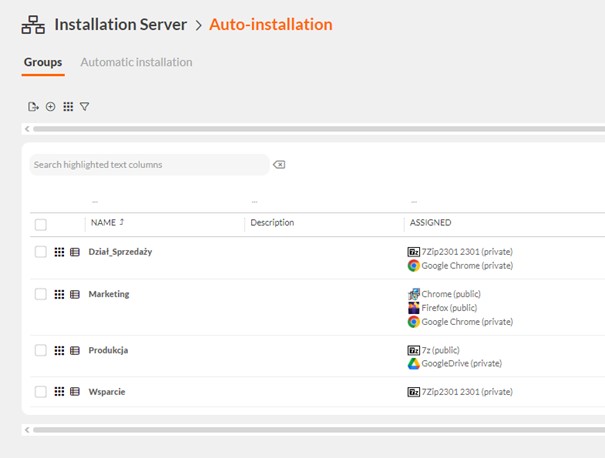
In the next step, the installation of packages was sent out and set as a cyclic task in the system. This way, the system will cyclically check whether the desired software is present on the machines in question and install it when needed. In the above way, the unit has raised its security standards by subscribing to the rules of the NIS2 directive.
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: Does NIS2 require monitoring of suppliers for cyber security?
Yes, entities must regularly assess the risks associated with their suppliers and business partners. NIS2 introduces the need to monitor all entities in the supply chain to ensure that they meet appropriate cybersecurity standards.
Question 2: What are the risks of suppliers not being NIS2 compliant?
Failure of suppliers to comply with NIS2 can lead to serious security vulnerabilities that can be exploited for cyberattacks. Companies are responsible for the security of their supply chains, which means they must implement appropriate procedures and tools to monitor suppliers.
Question 3: What steps can I take to ensure that my business partners are NIS2 compliant?
Above all, conduct regular security audits, implement service level agreements (SLAs) related to cybersecurity, and require incident reporting from vendors. Monitoring activity and putting appropriate safeguards in place is key to compliance with NIS2 regulations.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!