NIS2 #5: Control of used applications and PROCESS policy
NIS2 application control and PROCESS policy implementation
NIS2 in a nutshell
Is your entity ready for the new cyber security regulations under NIS2? These changes could have a huge impact on your business, regardless of your industry. In this email, we’ll outline key information you should know and help you understand how the new requirements could affect your entity. Learn the latest market news and what to do to ensure full compliance with the new regulations!
NIS2 – Is your entity ready for new regulations and cyber threats?
According to market research, many entities are still unaware of the full scope of the changes brought by NIS2. According to a recent report by Veeam, as many as 40% of entities have not yet taken any steps to implement NIS2 requirements, despite the fact that the risk of cyber threats is growing. Implementing appropriate IT security standards is becoming not only a legal requirement, but also an important part of building customer trust and maintaining operational stability in the face of increasing cyberattacks. Don’t wait- take action now!
How to meet NIS2 requirements with eAuditor?
Control of used applications and PROCESS policy
USE CASE
In connection with the implementation of the NIS2 Directive regulations in the unit, it has become necessary to control the applications used by users. The provisions of the NIS2 Directive stipulate the need to ensure that the applications used in the entity on all end machines meet the security and expediency requirements of the institution. The application of control of the applications used through the PROCESS policy responds to the requirements of Article 21 by eliminating the risks arising from unauthorized software. The unit therefore decided to use the Auditor system and Hyprovison DLP to block the use of unwanted applications and portable applications.
- A system agent was installed on the computers.
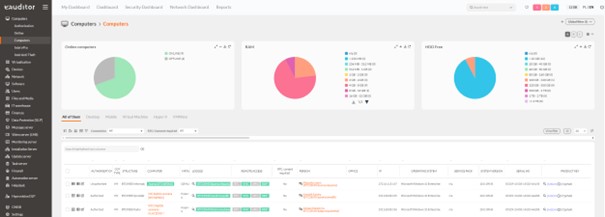
- The eAuditor system has prepared and propagated software schemes. It allows you to create permissible and forbidden schemes for more than 4,000 applications recognized by the system.Thanks to the settings, the system will automatically and immediately take the operation of uninstalling forbidden software as soon as it is detected.
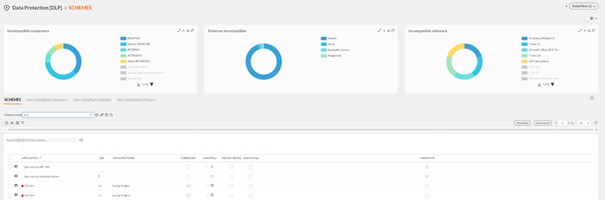
Then, using the PROCESS policy in Hyprovision DLP, potentially dangerous and unwanted portable applications were blocked.
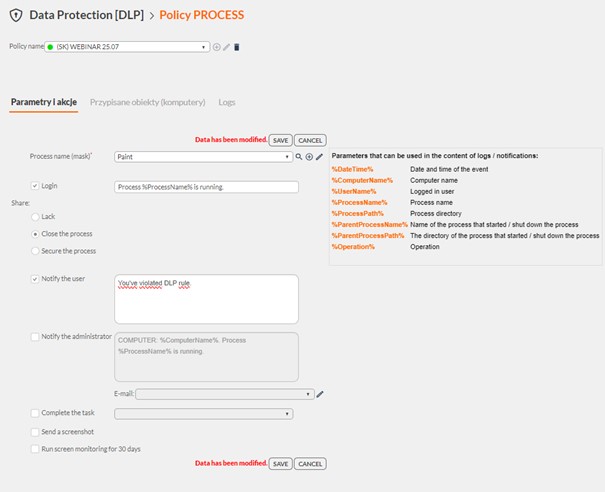
Such a setting will block unwanted applications from running, regardless of their detection by the system.
In the above way, the unit has raised security standards by subscribing to the rules of the NIS2 directive.
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: What steps should I take to implement NIS2 in my company?
To implement NIS2, you must first conduct a risk analysis, implement appropriate IT security management policies, update security and monitoring systems, and establish incident reporting procedures. It’s also a good idea to use tools that support risk management, such as monitoring and privilege management systems.
Question 2: What are the main differences between NIS2 and the advance directive?
NIS2 expands responsibilities to more sectors and imposes stricter requirements for risk management and incident reporting. NIS2 introduces higher penalties for non-compliance and extends responsibility to company boards, not just IT teams.
Question 3: How does NIS2 affect collaboration with suppliers and business partners?
NIS2 requires that companies not only secure their systems, but also ensure the security of suppliers and business partners. Collaboration with third parties must comply with NIS2 guidelines, and companies are required to monitor risks throughout the supply chain.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!