NIS2 #4: DLP Policies.
Management of DLP policies in accordance with NIS requirements
NIS2 in a nutshell
Implementing NIS2 can be a challenge, but with the right financial support it will definitely be easier. That’s why it’s worth knowing that there are funding programs available that can help your entity comply with cyber security requirements. Discover key information about NIS2 and take advantage of funding opportunities.
Funding for implementation of NIS2 requirements
The European Union offers various financial support programs that want to implement NIS2-compliant cybersecurity measures. One example is the “Deployment Actions in the area of Cybersecurity” competition (DIGITAL-ECCC-2024-DEPLOY-CYBER-07) under the Digital Europe program , which supports the implementation of cybersecurity solutions. This is an excellent opportunity to obtain funding for the introduction of modern IT systems, such as eAuditor. Read whether your entity is eligible for financial support and find out how to obtain funding. Applications must be submitted electronically through the EU Funding & Tenders Portal. The deadline for submitting applications is January 21, 2025. Funding is typically 50% of project costs, with up to 75% support for SMEs, which can assist private and public entities in meeting the requirements of the NIS Directive More about available funding -. Read the document
How to meet NIS2 requirements with eAuditor?
DLP Policies
USE CASE
In connection with the implementation of the NIS2 Directive’s provisions in the unit, it has become necessary to control the websites visited by employees and eliminate potentially dangerous sites. The provisions of the NIS 2 Directive stipulate the need for specific protection measures provided against accidental visits by employees to potentially dangerous sites or sites with unauthorized or unknown content. This corresponds to the requirements of Article 23 of the Directive for detecting and eliminating risks associated with access to malicious websites. To this end, the unit decided to implement the Hyprovision DLP solution.
- A system agent was installed on the computers.
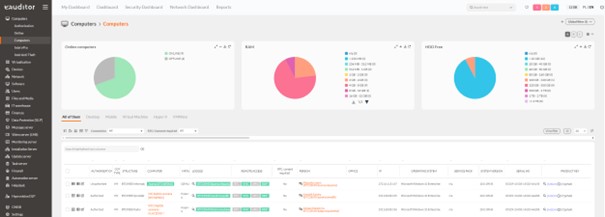
- Agent configuration including web monitoring was distributed to computers.
- The Hyprovision DLP system has configured a WEB policy setting only business category websites classified by the eAuditor system’s AI as allowed
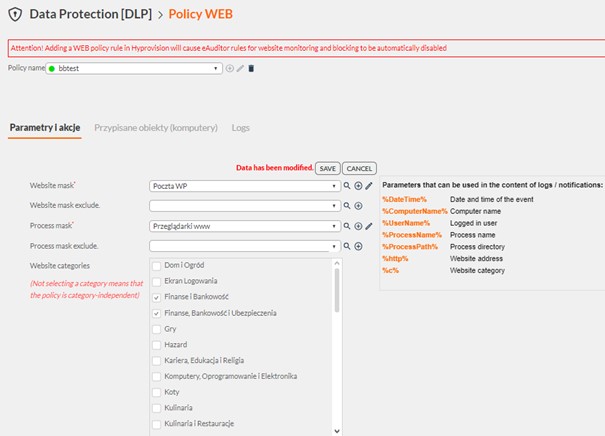
The policy was set to block all other sites.
This allowed the unit to monitor and control the Web sites visited by all employees and block sites visited with a specific category, thanks to built-in AI models.
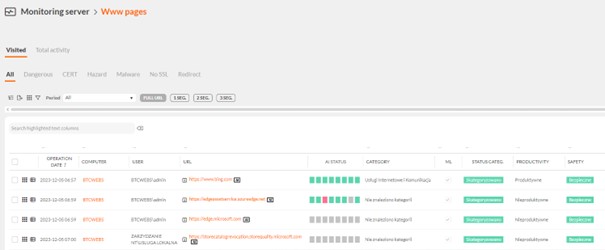
In the above way, the unit has raised security standards by subscribing to the rules of the NIS2 directive.
Learn more about controlling used applications in the eAuditor system -. https://www.eauditor.eu/blokowanie-aplikacji/
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: How can I effectively monitor employee activity in accordance with NIS2?
In order to meet NIS2 requirements for monitoring employee activity, it is necessary to implement tools that enable real-time oversight of user activities on IT systems. Software such as eAuditor offers real-time activity monitoring functions to track employee activities, analyze access to sensitive data and quickly detect potential threats. This makes it possible to minimize the risk of internal incidents and increase the security level of the entity.
Question 2: Can the eAuditor system help automate incident reporting?
Yes, eAuditor offers functions to automatically monitor incidents and generate reports that comply with NIS2 requirements. The system collects data on user activities, monitors suspicious behavior and can automatically generate incident reports that comply with the directive’s guidelines. This greatly simplifies the process of reporting and documenting incidents, making the company more efficient in managing cyber threats.
Question 3: How does the NIS2 affect employment and employee training policies?
NIS2 requires companies not only to put in place technical security measures, but also to ensure that employees are educated and trained in cyber security. Employees should be trained regularly to recognize threats, follow internal security policies and know how to respond to potential incidents.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf
Ensure NIS2 compliance now and protect yourself from high fines and cyber threats that are becoming a daily occurrence in the business world!