NIS2 #3: Control of applications in use
Effective application control in accordance with NIS2
NIS2 in a nutshell
Many entities are wondering whether the implementation of NIS2 requirements is really necessary and what costs and benefits are involved. Opinions are divided, and some businesses view it as quite a challenge, especially financially. However, one thing is certain – failure to act can have serious consequences, both legally and financially.
How do entities assess the need for NIS2 requirements?
Key challenges and prospects for the organization
Many entrepreneurs express doubts about whether their entity actually needs such advanced security features as NIS2 requires. The issue that comes up most often is the costs associated with implementing these solutions. In an era of tight IT budgets, some entities say they don’t have enough money to invest in cyber security. However, it’s worth remembering that implementing NIS2 is not just a formality – it’s a key step in protecting infrastructure from growing cyber threats. Failure to have adequate safeguards in place can expose an entity to serious risks of data loss, cyber attacks and hefty financial penalties.
How to meet NIS2 requirements with eAuditor?
Control of used applications
USE CASE
In connection with the implementation of NIS2 regulations in the unit, it became necessary to control what browsers employees use to visit the unit’s corporate website and work on the office system’s web console. This is because it became a problem for employees to use an outdated web console and an unsecured Internet explorer browser to log in. So the unit took measures to prevent such operations. This was in response to the requirements of Article 21, mandating the elimination of risks arising from unauthorized software. To this end, the unit decided to implement an eAuditor solution.
- A system agent was installed on the computers.
- An agent configuration including www monitoring was sent out to the computersThe system was set to a Configuration including monitoring of all visited sites, specifying them as “*”. The symbol in* system means everything. At the same time, the Internet explorer process was indicated as monitored.
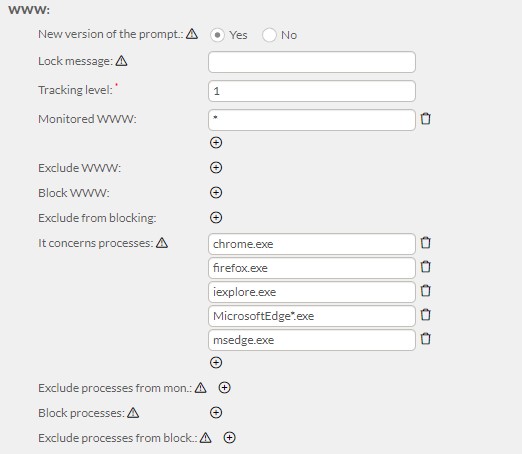
This allowed the Unit to monitor and control the web browsers used for certain purposes. This is because from now on, the use of Internet explorer to open the company’s website will be blocked.
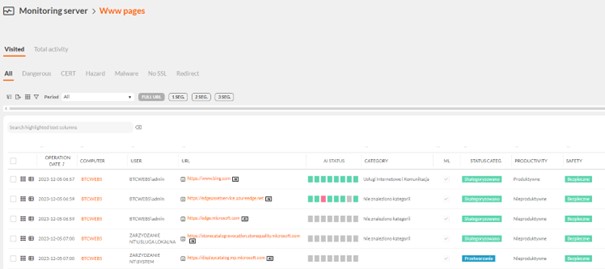
In the above way, the unit has raised security standards by subscribing to the rules of the NIS2 directive.
Learn more about controlling used applications in the eAuditor system -. https://www.eauditor.eu/blokowanie-aplikacji/
NIS2 – Meet answers to questions
Q&A section
Due to numerous questions about NIS2, we have prepared a comprehensive list for you, in which we answer the most pressing issues related to the directive.
Question 1: Does implementing NIS2 require a complete overhaul of my IT system?
No, implementing NIS2 does not always require a major overhaul of the IT system. In many cases, existing infrastructure can be adapted by introducing additional solutions, such as risk management, incident monitoring and increased security. Tools such as eAuditor allow IT systems to be adjusted quickly without the need for a complete overhaul, helping to effectively meet the directive’s requirements.
Question 2: What business benefits will come from complying with NIS2 requirements?
Meeting NIS2 requirements is not only a matter of compliance, but also an investment in the future of your entity. Business benefits include: better data protection and minimizing the risk of cyber attacks, building trust with customers who expect their data to be adequately protected, increasing competitiveness as NIS2-compliant entities are perceived as more trustworthy and professional, avoiding financial penalties associated with breaches of regulations
Question 3: Does NIS2 require continuous IT security monitoring?
Yes, as required by NIS2, entities must continuously monitor their IT systems to quickly detect and respond to security incidents. The directive emphasizes proactive risk management, meaning that regular monitoring, threat analysis and incident reporting are essential to ensure compliance and protection against cyber attacks.
NIS2 Essentials – useful links and resources
Want to learn more about NIS2 and the regulations that may affect your entity? We’ve put together the most important resources for you to help you better understand the upcoming changes.
- EU Parliament and Council Directive 2022/2025: Read the official NIS2 document
- The latest information about NIS2 on Biznes.gov.pl: Check what obligations you have to meet
- Directory of BTC systems that will help you comply with the NIS2 directive – Read -. https://www.eauditor.eu/dyrektywa-nis2-odpowiedz-unii-europejskiej-na-rosnace-cyberzagrozenia/
- Law on National Cyber Security System -. https://isap.sejm.gov.pl/isap.nsf/download.xsp/WDU20180001560/U/D20181560Lj.pdf