Monitoring of employees’ computers
- Activity Monitoring
- Computer Monitoring
- Website Monitoring
- Document Monitoring
- Print Monitoring
Table of contents

Monitoring of the employee’s computer
Monitoring an employee’s computer works well for monitoring the performance of individual employees, but also allows you to protect your computer workstation from malicious programs. Thanks to the system, managers can find out which programs are used most often by employees, and which software can be abandoned altogether (thus introducing savings to the organization). Modern monitoring systems allow certain activities and programs to be blocked. The most extensive and advanced programs allow detailed monitoring of devices and authorization and monitoring of USB drives. This is an excellent mechanism to fully protect confidential data. In any company, it is worth betting on reliable monitoring of the employee’s computer, so you can protect yourself from dangerous actions by hackers.
Example implementation of employee computer monitoring functionality
Organization X employs an average of 250 people at its headquarters. Its representative Mr. Kowalski was not able to control all of his employees and, most significantly, did not have full access to the data exchanged and sent from their computers. Wanting to ensure the full use of working time and the proper use of the work tools provided to the employee, he decided to use a special tool that allows him to secure data.
Benefits
The key to successful monitoring of an employee’s computer is choosing the right program and implementing it. Both free and paid monitoring applications are available on the market, so everyone can find something that is suitable for their industry and the size of their company. It is worth paying attention not only to programs that allow monitoring of selected computers, but also those that allow monitoring of the company’s network. Thanks to this, the administrator of the company’s network, will be able to monitor the flow of data between all computers in real time.
Monitoring an employee’s computer
Monitoring computers and networks is as legal as possible, but be sure to use the right software to manage your IT environment (hardware, networks, operating systems, software and users). The monitoring system must comply with Polish law, as well as EU law and generally accepted RODO standards.
Organizations or small businesses, wishing to install a computer monitoring program, should remember to inform their employees in advance. Such information should be included, first of all, in the work regulations. Monitoring an employee’s computer is an excellent choice not only for organizations, large corporate companies, but also for small entrepreneurs.
Which employee computer monitoring program to choose?
BTC is a producer of IT software. It offers a system – eAuditor. It is a tool that enables professional management of IT resources and constant supervision of data security in the organization. It supports and complements the company’s strategic management processes, providing the ability to grow flexibly and efficiently. Our tool is an ideal solution for organizations, large companies, as well as smaller businesses.
As a result of the implementation of the system, the client gained benefits such as effective monitoring of working time, the ability to automate the workday by analyzing the processes performed and responding in real time to various needs. Monitoring of employees or computers also helps to rationally plan tasks to be performed for an employee. It also has an impact on financial savings, as the client has the ability to determine which resources are necessary in the organization and to what extent they are used. Complete and up-to-date information on IT infrastructure ensures optimal investment in this area and generates savings of up to 40%.
The eAuditor, in addition to extensive functionality that includes:
- Monitoring of employees and computers,
- Inventory of computers and IT infrastructure,
- Remote management of computers,
- Analyze IT security key indicators (SOC) (Dashboard, Security Dashboard, Network Dashboard, My Dashboard),
- BitLocker Remote Disk Encryption.
The eAuditor is a modern tool that is fully web-based and responsive. This allows you to access the console from anywhere on earth and from any device with a web browser. Updates are automatic and ensure that the system is always up-to-date. Among other things, the system allows monitoring of the following.
Activity monitoring
An administrator in the eAuditor system console can verify what activities an employee performs as part of his or her job duties. It analyzes his working time on an ongoing basis, among other things, employee’s computer logins, launched pages, devices, files and printed documents. The eAuditor software therefore allows comprehensive control of employee activity and analysis of their productivity based on the data.
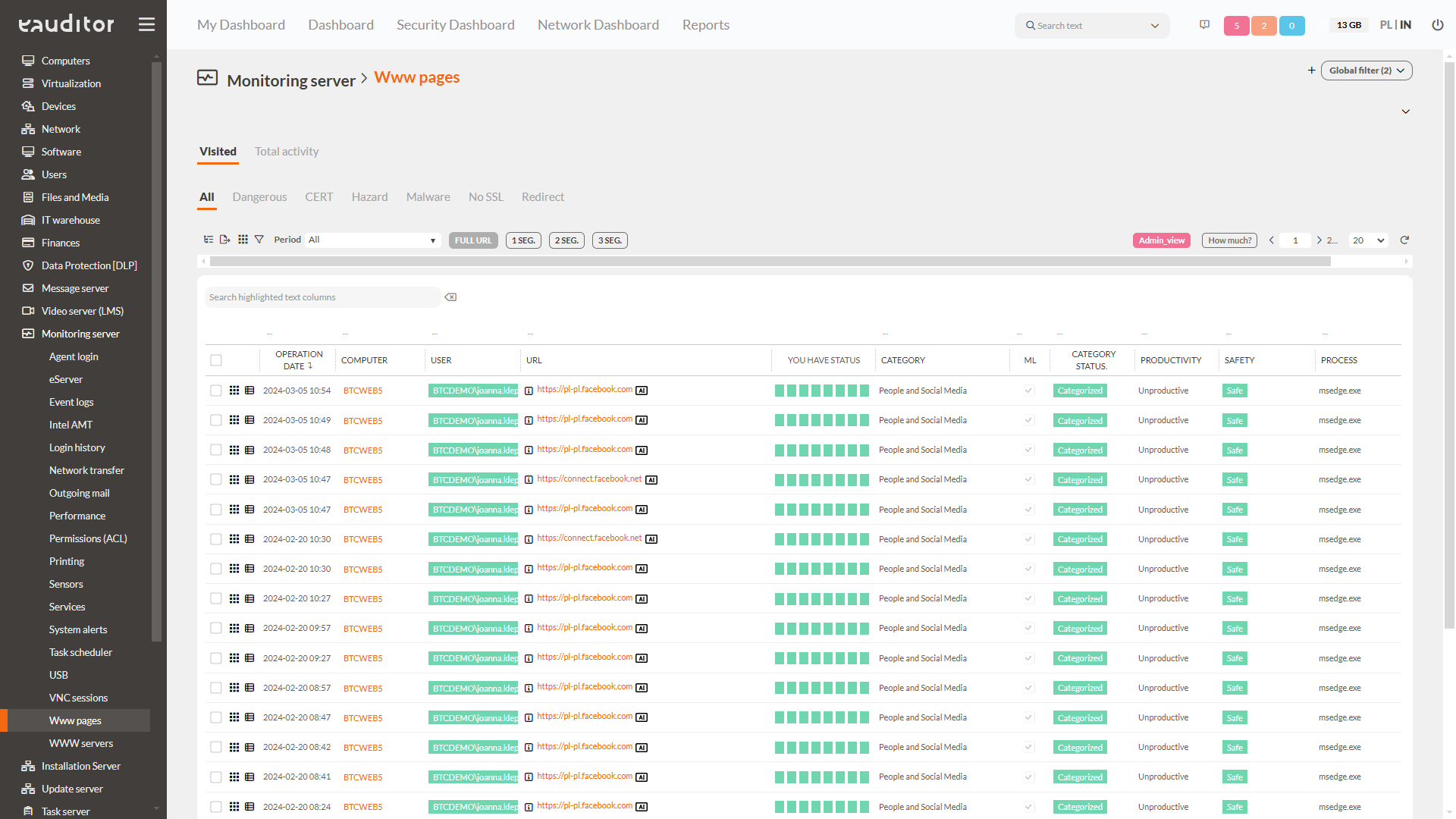
Web monitoring
The eAuditor system also allows monitoring of websites visited by employees, ensuring a high level of IT security. The administrator receives information about, among other things, the status of website classification. In addition, the system informs him, among other things, about indicating the category of the site, its presence on the CERT list or gambling sites.
Document monitoring
In the eAuditor system, it is possible to monitor the documents on the employee’s computers. The administrator can see every action performed on the document: modification, deletion, or its imprinting. With a few clicks, the administrator will also generate handover protocol (PP), return protocol (PZ) and PZ+PP (return and handover protocol). Thus, he has quick access to the necessary information, registering and de-registering documents in the console.
![Data Protection [DLP] Rules and logs](https://www.eauditor.eu/wp-content/uploads/2020/05/Data-Protection-DLP-Rules-and-logs.png)
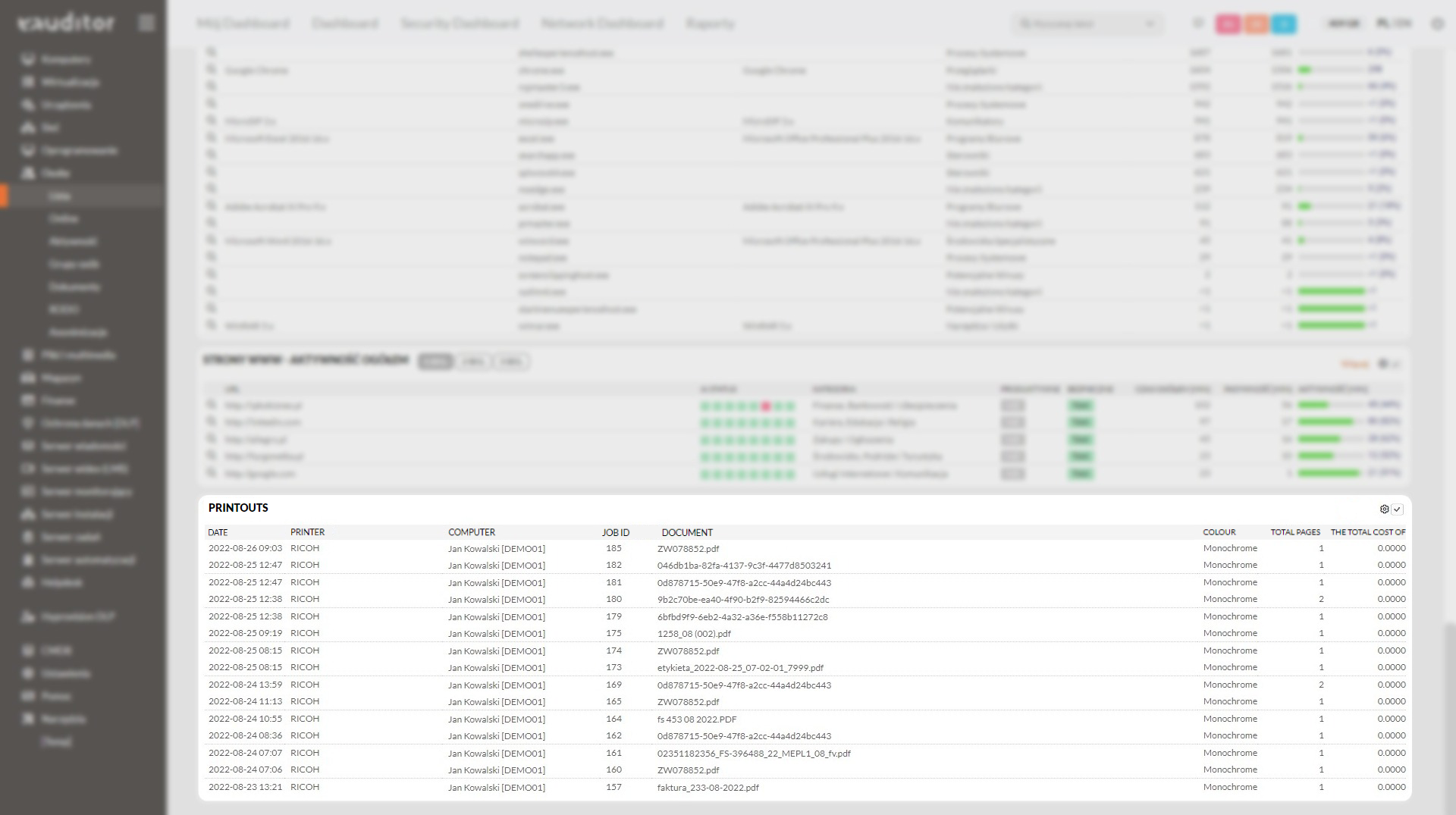
Monitoring of printouts
In the eAuditor system console, the administrator can also monitor the employee’s printouts. This is possible with the WorkTime Manager functionality. With its help, it is possible to check:
- document name,
- number of pages,
- types of printout (color/monochrome),
- date of printing,
- the cost of the printout.
Want to learn more about this functionality? Watch our video “Monitoring employee work”


