Application monitoring
Learn how to effectively monitor the activity of running applications
Application monitoring – employers’ obligations
Employers should inform employees about monitoring the performance of applications on their work computers. Most importantly, this must be done before real-time monitoring of applications and computers begins. Employees should therefore sign relevant regulations or statements.
Monitoring of Internet applications and computers is possible as long as the following conditions are met:
- the employer has informed employees about the use of such a form of control of their work (e.g. in the regulations);
- checking of activity is not permanent;
- the monitoring concerns a group of employees and not just an individual user, unless there is a legitimate rationale for this type of action.
Benefits of application monitoring
Among the main benefits of application monitoring located on company computers can include:
- increasing employee productivity – application monitoring makes it possible to determine how employees use computer programs. In particular, this applies to activities unrelated to work duties. Such practices, in addition to reducing employee productivity, can threaten the security of the organization,
- eliminate ineffective applications – monitoring allows you to assess the effective use of business applications. If selected applications are not used by employees or are used to a negligible degree, the IT administrator can decide to stop using them. The data collected in the system allows a decision to optimize the licenses held. And, consequently, reduce software maintenance costs.
- increase security – the administrator, through monitoring, can check the use of portable applications, which are often vulnerable to malware attacks. They are a potential source of data leakage, against which, thanks to this functionality, we can protect ourselves.
How to monitor application activity and performance in the eAuditor system?
The process of monitoring applications in the eAuditor system is done as follows. We start it by setting up the appropriate configuration and then sending it to the designated computers.

Once the functionality is enabled, the eAuditor system will start generating a list of all running applications and processes. The system will classify the processes both in terms of the time they were started, the time they were stopped, and the total time the application was used.
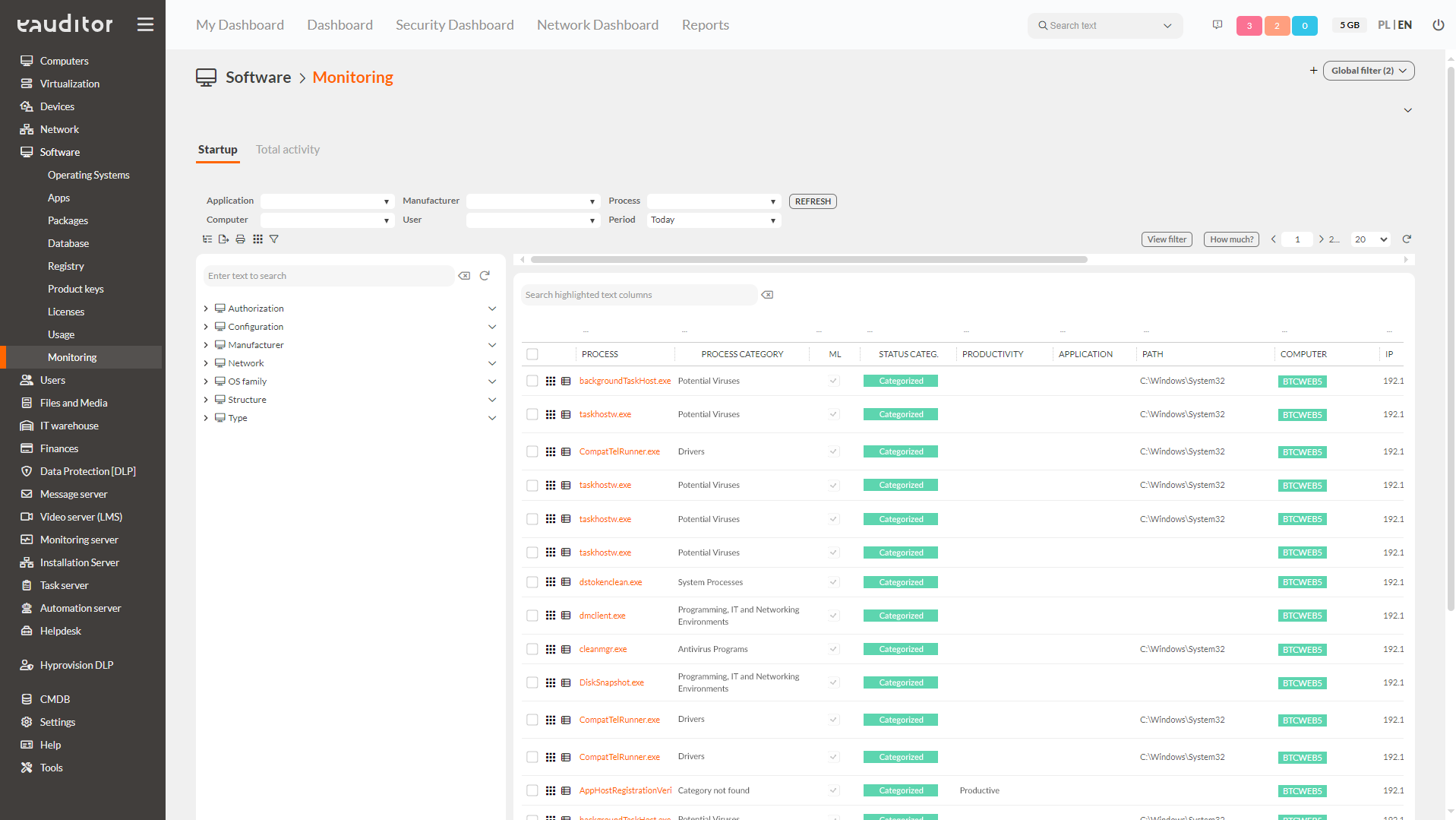
In addition – by analyzing the degree of use of a given application – the system will indicate how long the user had the application running and for how long he actively used it.
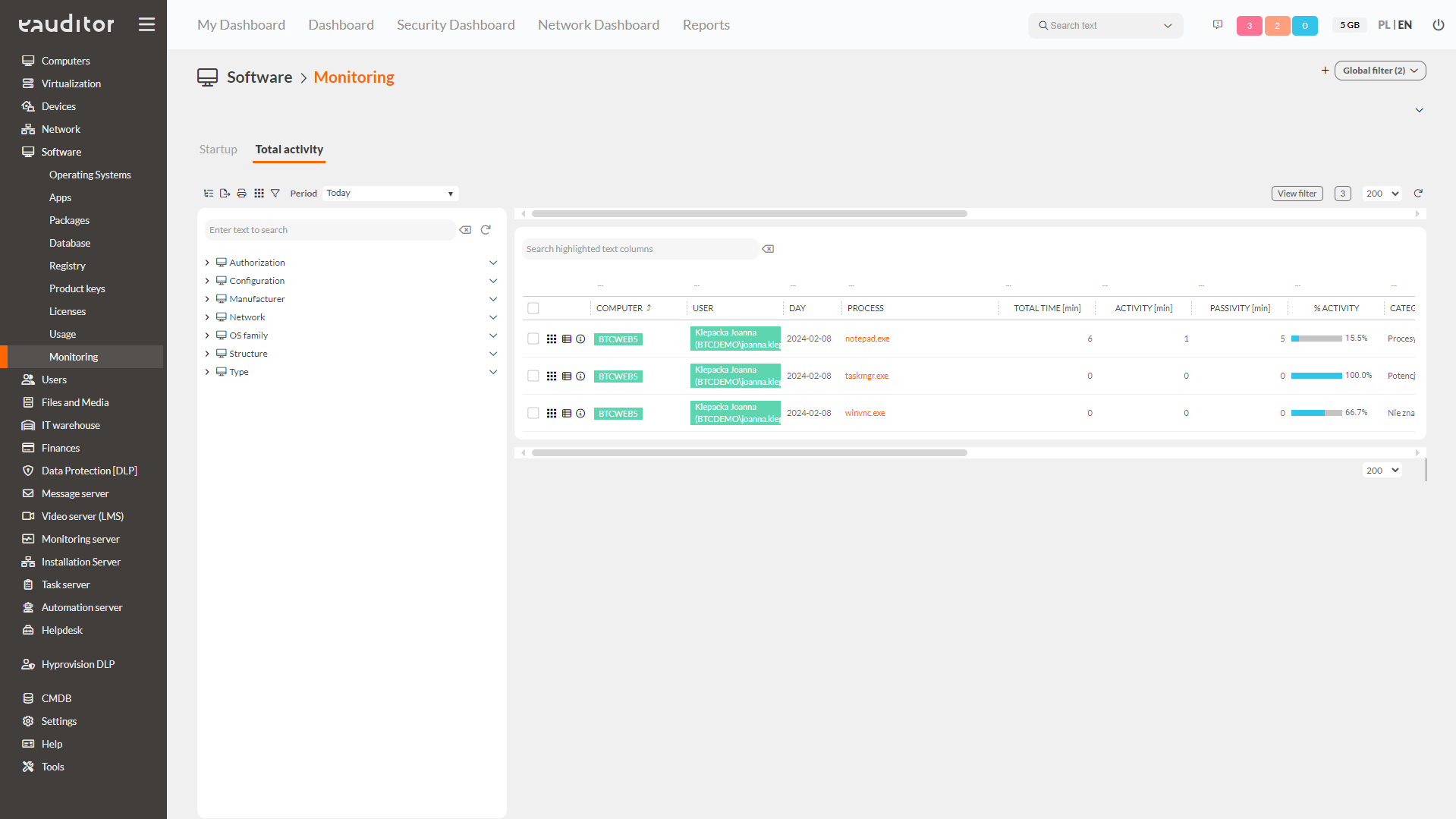
What’s more, if the selected application has the ability to work in multiple windows, the system will tell us which windows are active and for how long. Using the Word application as an example, the system tells us which documents are open and how long the user has been using them. We will get the same result when monitoring all text applications.





