Main functions
Benefits
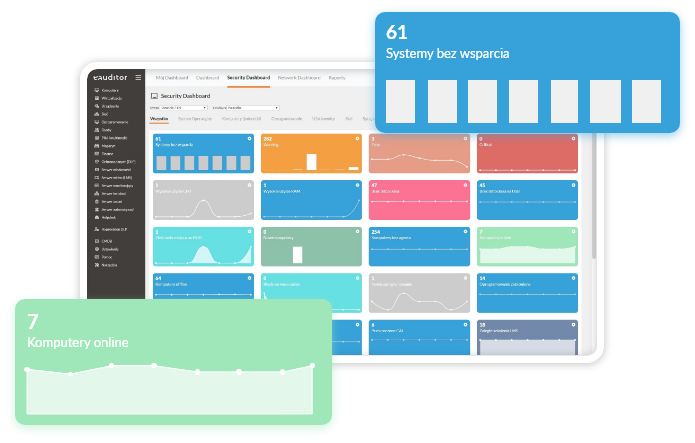
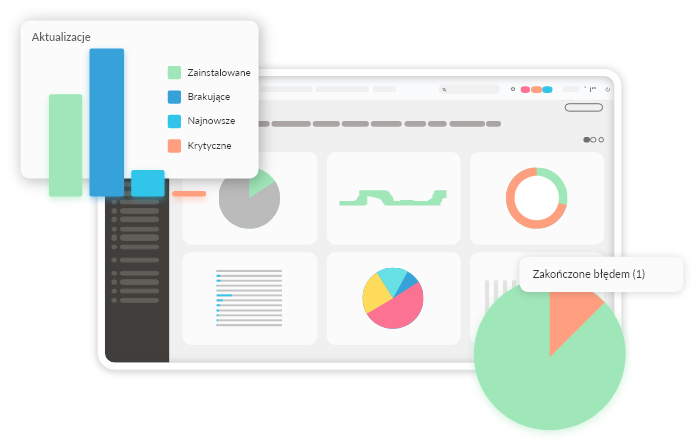
Monitoring of computers
Monitoring
computers
FULL a control and security – monitoring employee computers
has never been so easy.
PFULLa controla and security – monitoring employee computers has never been so easy.
Streamline management and secure your computers with eAuditor
Data protection and increasing IT security
Automatic monitoring of resources
Optimization efectefficiency
Audit automation


Ensure compliance with rules and regulations
Improving labor standards
Zdditional supporte technical support
Cost reduction
Monitor computers remotely and outside your local IT network with eAuditor
– full visibility and data protection, even behind NAT
Monitor computers remotely and outside your local IT network with eAuditor – full visibility and data protection, even behind NAT
Monitoring of computers in the eAuditor system includes inventory of technical parameters, configuration, installed software, files, monitoring of user activity, such as logging in, launching applications, visiting a website, printed documents, connected devices, opened files. Monitoring also includes analysis of parameters affecting IT security: disk encryption, status of patches and updates, creating, modifying and deleting files, sending files to clouds, etc.
Yes, it is legal to monitor computers as long as the employer informs employees about the monitoring while complying with relevant privacy laws.
Yes, employees must be effectively informed about monitoring. Effective information is one where the Employer will ensure accountability of the process (i.e., preferably in writing). An employee may refuse to sign an information document, but this does not affect the Employer’s authority to monitor. It is recommended that Employers specify the scope and purpose of monitoring when informing.
Benefits include improved data security, optimized productivity, regulatory compliance, IT asset management and early threat detection.
Yes, the eAuditor system can inventory and monitor computers on the local network, VPN and computers outside the local IT network (behind NAT). The monitored computers do not need to be permanently connected to the eAuditor system server – periodic access to the Internet is sufficient.
Yes, the eAuditor system allows you to customize the level of inventory and monitoring according to the needs of the entity, allowing you to configure monitoring policies for different roles and departments and users.
Collected data is secured by means of encryption, access control (a multi-level system of access to the eAuditor application and its various options) and advanced security mechanisms in the system itself. The eAuditor system is subject to regular vulnerability tests performed by specialized and independent entities.
The eAuditor system does not adversely affect computer performance, running in the background (transparently to users) without noticeable slowdowns.
© Copyright 2024 BTC Sp. z o.o. | www.btc.com.pl | All Rights Reserved | Cookie policy | Principles of personal data processing | Contact